Table of Contents
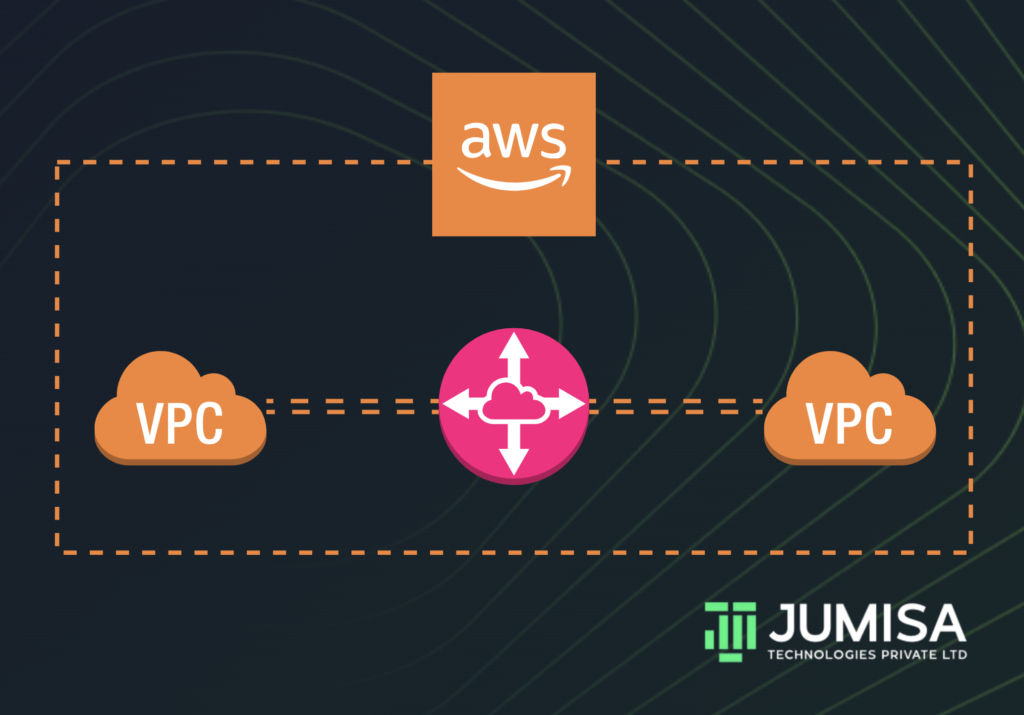
What is VPC Peering?
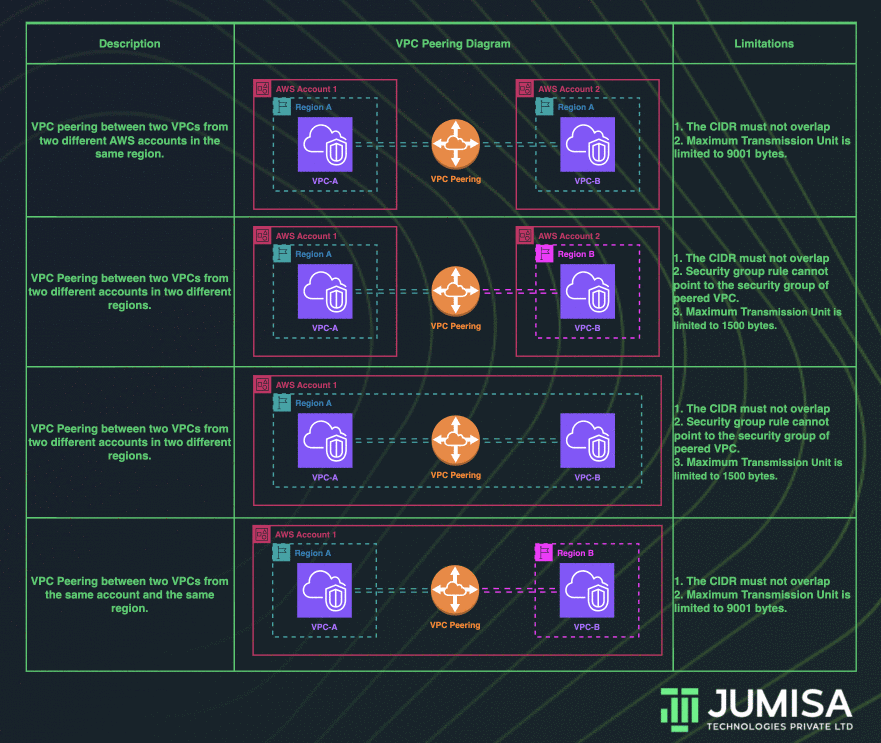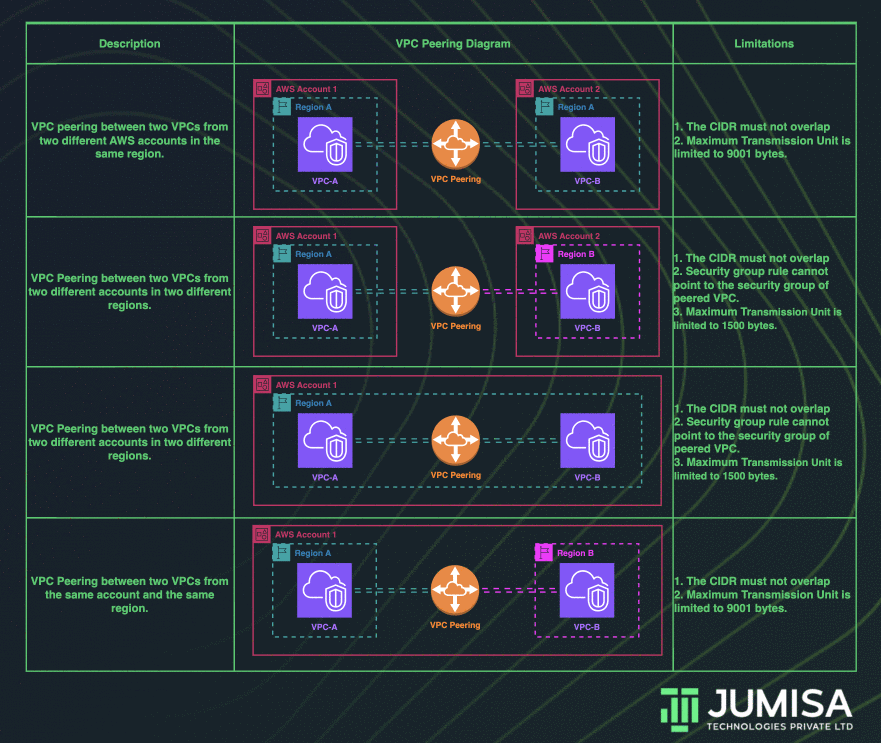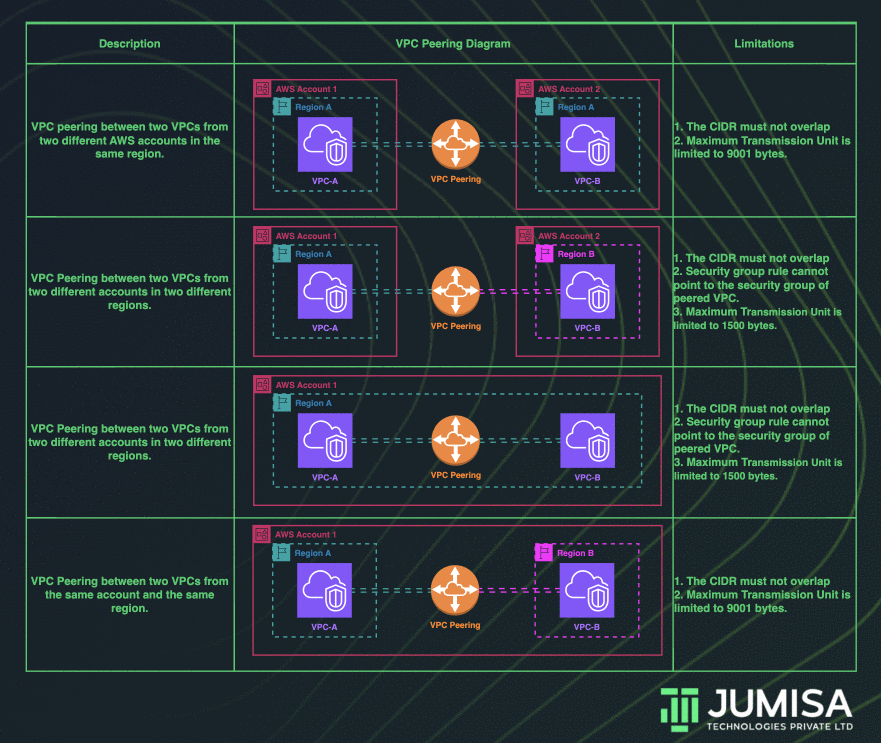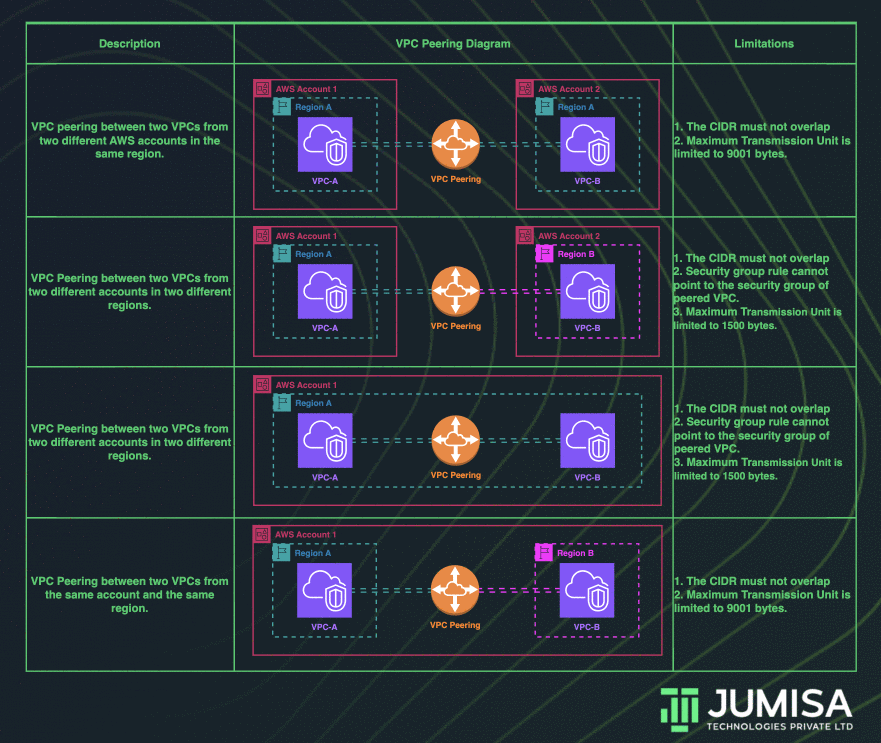
VPC peering connection enables us to route traffic across multiple VPCs using private IP addresses. Instances from different VPCs can communicate with each other as if they are within the same network. We can create a VPC peering connection between the VPCs in the same account, or between VPCs across different AWS accounts. Similarly, VPC peering can be done in the same region or across multiple regions.
Overview:
Using VPC peering, resources in the VPCs in different AWS Regions can communicate with each other using private IP addresses, without using a gateway, VPN connection, or network appliance. All inter-Region traffic is encrypted with no single point of failure or bandwidth bottleneck. The traffic remains in the private IP space on the global AWS backbone and never traverses the public internet. Hence it is a secure and cost-effective way to share resources between regions or replicate data for geographic redundancy.
Requirements for a VPC peering connection:
The requirements to establish a VPC peering connection between multiple VPCs:
- The VPCs that are to be peered cannot have a CIDR block that overlaps with one another.
- A request from the requester VPC to the accepter VPC must be approved to create the VPC peering connection. The accepter VPC can be in the same or different AWS account.
- To enable the flow of traffic between the VPCs using private IP addresses, we must manually add a route to one or more of their VPC route tables that points to the IP address range of the peer VPC.
If required, update the security group rules that are associated with your instance to ensure that traffic to and from the peer VPC is not restricted. If both VPCs are in the same region, you can reference a security group from the peer VPC-As a source or destination for ingress or egress rules in your security group rules.
With the default VPC peering connection options, if EC2 instances on either side of a VPC peering connection address each other using a public DNS hostname, the hostname resolves to the public IP address of the instance. To change this behavior, enable DNS hostname resolution for your VPC connection. After enabling DNS hostname resolution, if instances on either side of the VPC peering connection address each other using a public DNS hostname, the hostname resolves to the private IP address of the instance.
Multiple VPC Peering connection:
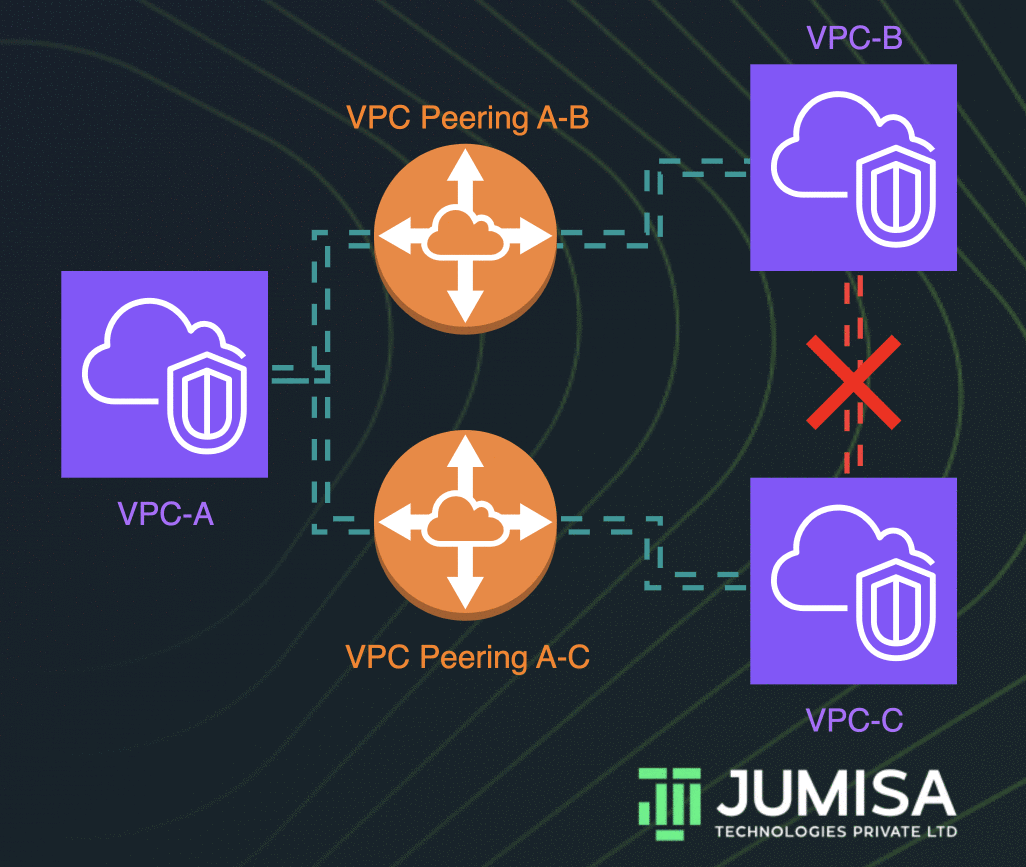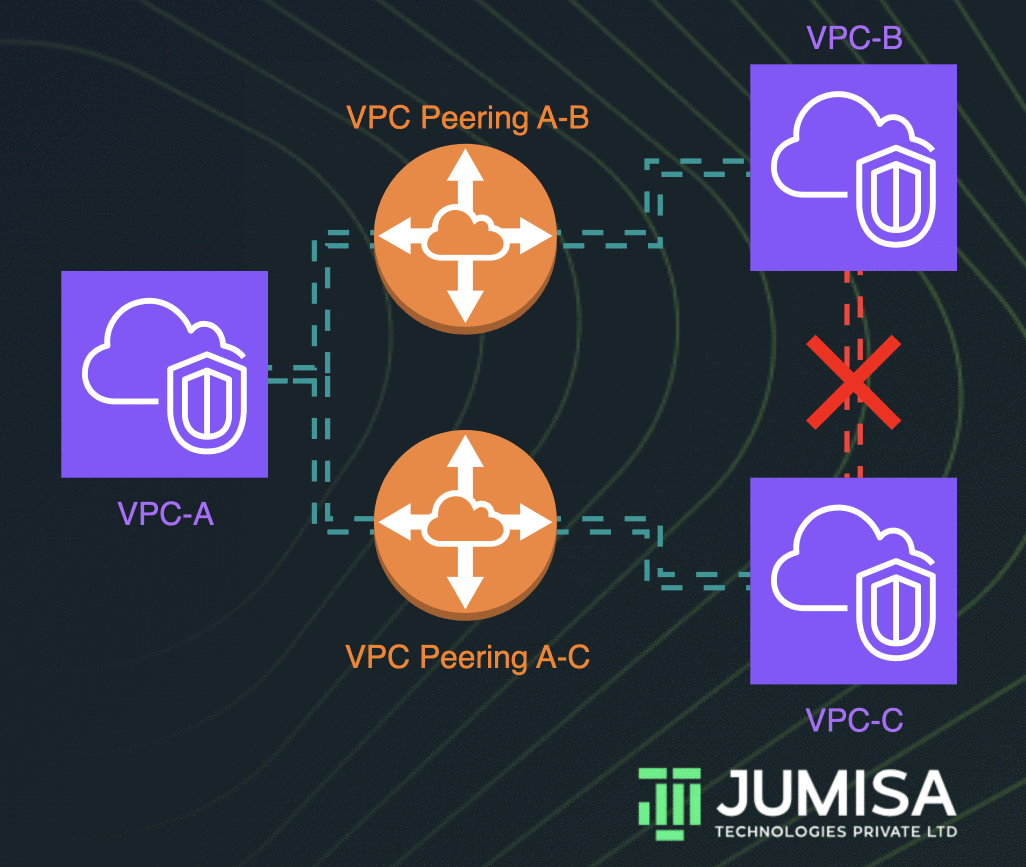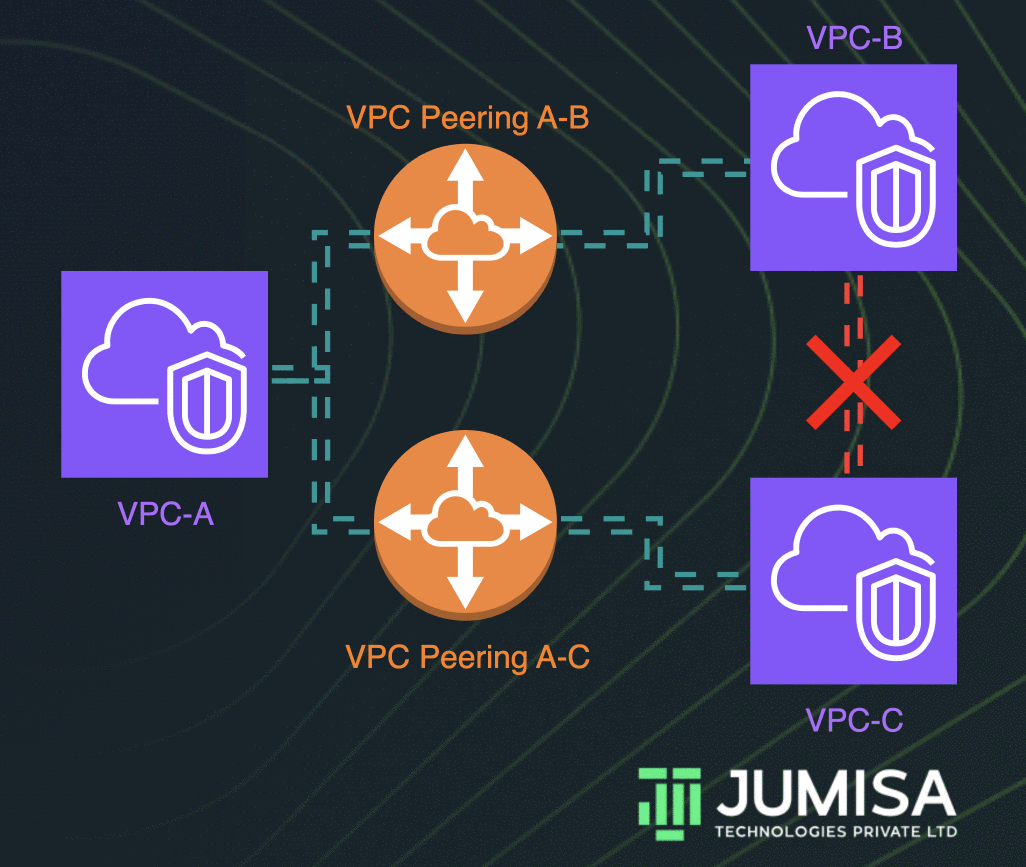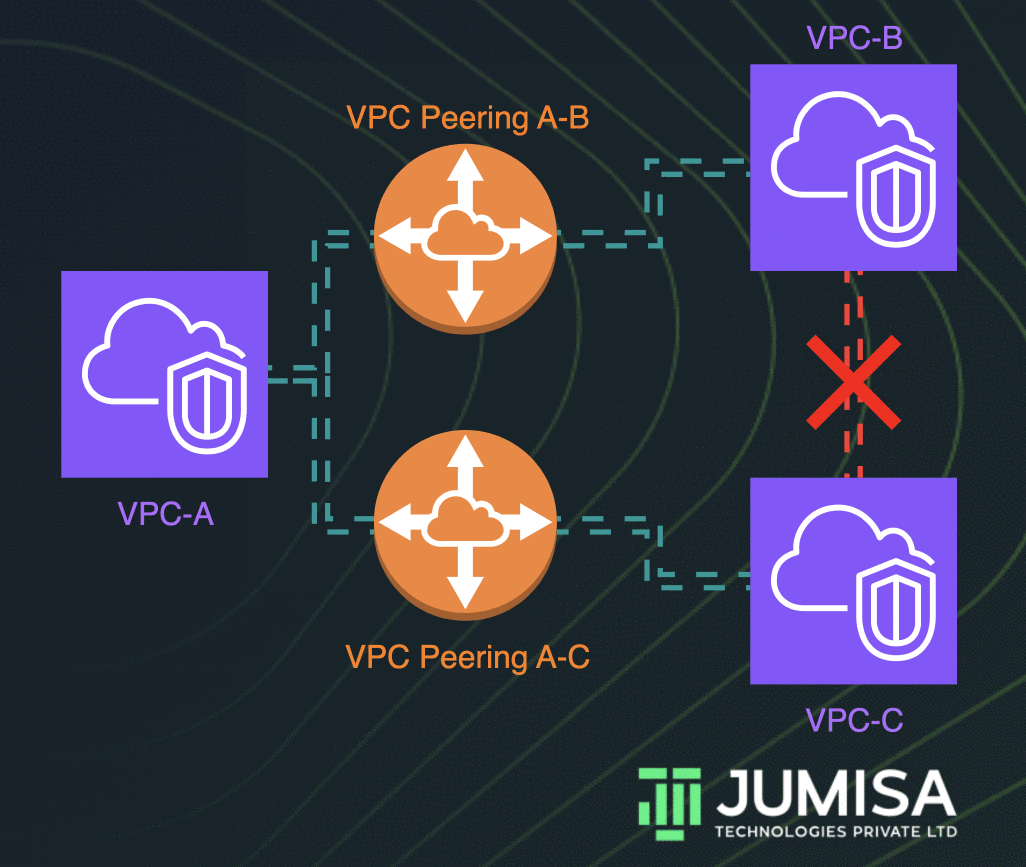
A VPC peering connection is a one-to-one relationship between two VPCs. We can create multiple VPC peering connections for each VPC. But there will be no communication between the VPC that is not directly peered with.
Limitations of VPC peering:
- VPC peering connection quotas
- Overlapping CIDR blocks
- Transitive peering
- Edge-to-edge routing through a gateway or private connection
- Inter-Region VPC peering connections
- Shared VPCs and subnets
1. VPC peering connection quotas:
- There are limits for VPC peering connections for an AWS account. However, we can request an increase for these quotas.
- The default active VPC peering connections per VPC is 50. This can be adjusted up to 125
- The outstanding VPC peering connection requests allowed per VPC is 25.
- Expiry time for an unaccepted VPC peering connection request is 168 hours (1 Week). Post this time, the request will be rejected. This time cannot be adjusted.
- You cannot have more than one VPC peering connection between two VPCs at the same time.
- If the IPv4 CIDR block of a VPC in a VPC peering connection falls outside of the private IPv4 address ranges specified by RFC 1918, private DNS hostnames for that VPC cannot be resolved to private IP addresses. To resolve private DNS hostnames to private IP addresses, you can enable DNS resolution support for the VPC peering connection.
2. Overlapping CIDR blocks:
- VPC peering connection between VPCs that have matching or overlapping IPv4 or IPv6 CIDR blocks is not possible.
- If there are multiple IPv4 CIDR blocks, and if any of the CIDR blocks overlap, you can’t create a VPC peering connection cannot be created even across the non-overlapping CIDR blocks.
- The resources on either side of a VPC peering connection can communicate over IPv6 only if an IPv6 CIDR block is associated with each VPC, the instances in the VPCs are enabled for IPv6 communication, and IPv6 traffic is routed for the peer VPC to the VPC peering connection.
3. Transitive peering:

VPC peering does not support transitive peering relationships.
For example, let us consider three VPCs VPC-A, VPC-B, and VPC-C among which the VPC-A is peered with VPC-B and VPC-C. Hence the VPC-A can communicate with the other two VPCs. However, the VPC-B cannot directly connect with the VPC-C since there is no peering between them.
4. Edge to edge routing through a gateway or private connection:
The network routes associated with a VPC cannot be used by the resources in the peered VPC. For example, let us assume two VPCs VPC-A and VPC-B are peered with each other.
- If VPC-A has an internet gateway, a NAT gateway, VPN connection or an AWS Direct Connect connection to a corporate network, or a gateway endpoint that provides connectivity to Amazon S3 to private subnets, the resources in VPC-B cannot send or receive traffic via any of the gateways or private connections or the endpoints in VPC-A.
5. Inter-Region VPC peering connections:
- It is not possible to create a security group rule that references a security group from peered VPC. For example, a security group rule in the VPC-A cannot point to a security group from VPC-B.
- For VPC peering connections in the same Region, Jumbo frames with a Maximum Transmission Unit (MTU) of up to 9001 bytes are allowed. But for the VPC peering connections across multiple regions, the MTU is limited to 1500 bytes.
- DNS resolution support must be enabled for the VPC peering connection to resolve private DNS hostnames of the peered VPC to private IP addresses, even if the IPv4 CIDR for the VPC falls into the private IPv4 address ranges specified by RFC 1918.
6. Shared VPCs and subnets:
The actions such as describe, create, accept, reject, modify, and delete peering connections are allowed only to the VPC owners. Participants cannot work with peering connections.









One Response