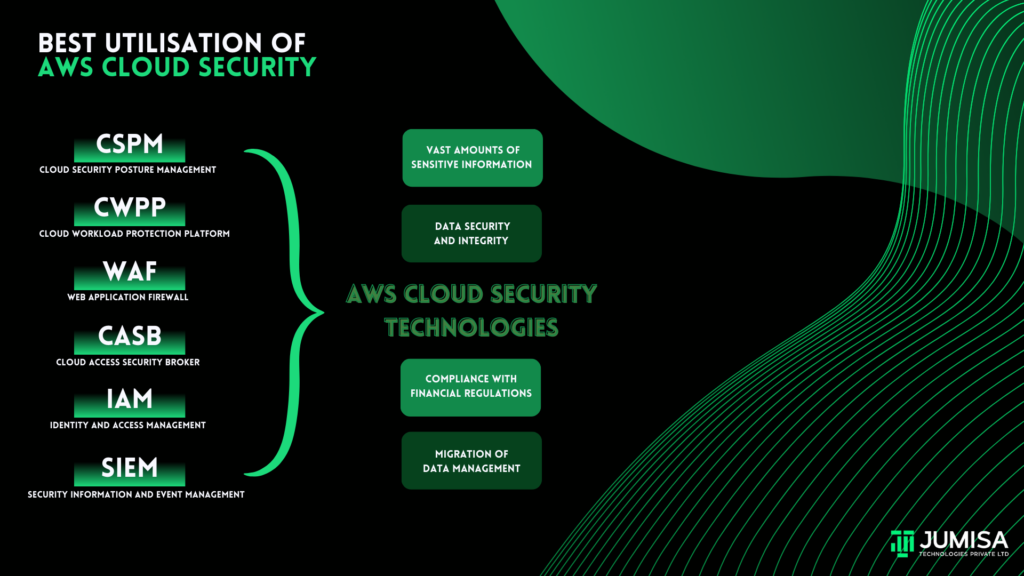
Your organization has to deal with vast amounts of data for Cloud Security Technologies, including sensitive and regulatory information. You also need to manage access of users to the data while maintaining its integrity.
The solution is to migrate data management to the AWS cloud due to its effective security technologies.
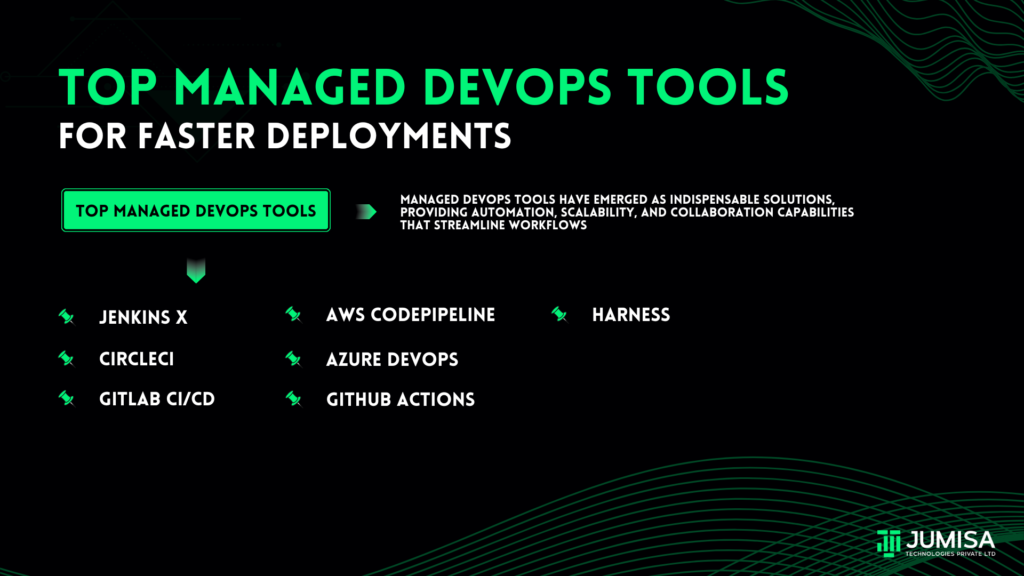
Problem scenario:
- An organization manages vast amounts of sensitive information including employee data, client data and financial records.
- An organization deals with a vast amount of sensitive financial data, including client transactions, account information and regulatory reports.
- The organization migrates data management to the AWS cloud to increase scalability, cost-effectiveness and data accessibility.
- However, it is necessary to ensure data security and integrity and manage access to data based on requirements.
- Furthermore, it is essential to ensure compliance with financial regulations such as GDPR during data management.
Solution:
Utilize AWS cloud security technologies
One main thing to understand is that AWS Cloud Security involves various technologies that are best utilized for specific security objectives within your AWS environment.
CSPM (Cloud Security Posture Management):
An organization’s cloud infrastructure is the most vital. AWS Cloud Security Technology CSPM involves using specialized tools and platforms to automatically assess the security configuration of cloud resources, such as virtual machines, storage buckets, databases, and networking components, across multiple cloud environments. This technology allows the user to continuously monitor the adherence to compliance.
Best utilization of the tool
- The security of the cloud is a shared responsibility between AWS and the user. CSPM enables the user to continuously monitor AWS configurations.
- CSPM ensures that security measures comply with best practices and regulatory requirements.
- CSPM allows the detection of any vulnerabilities and security risks across AWS accounts and services.
- CSPM automates the identification and remediation of misconfigurations.
- Bonus: If you integrate CSPM with AWS Config and AWS CloudTrail, you will gain visibility into changes and events that impact your security posture.
CWPP (Cloud Workload Protection Platform):
Cloud Workload Protection Platform or CWPP is a part of the AWS cloud security technology that acts as a scavenger for any security disruption for workloads and applications running in cloud environments. Technically, CWPP offers several security aspects that address the difficulties of an organization.
Best utilization of the tool
- A significant function of CWPP tool is to scan the cloud workloads and detect malware and other malicious software that can compromise the integrity of the cloud environment. Hence, CWPP provides stringent antimalware protection.
- CWPP tool also scans the network traffic and system activity for intrusion detection and prevents unauthorized access attempts.
- CWPP monitors any changes applied to a sensitive / critical file and alerts administrators to any unauthorized modifications that could indicate a security breach.
- Furthermore, you can integrate CWPP with AWS Security Hub for any security breaches and incident response.
WAF (Web Application Firewall):
Web application firewall or WAF is a frontline protector of a web application that scrutinizes the incoming web traffic. In simple terms, it checks every visitor to ensure no suspicious activity is taking place.
Best utilization of the tool
- You can utilize AWS WAF to scan every data and user visiting the web page.
- You can also utilize WAF to protect APIs hosted on AWS against common security threats and vulnerabilities.
- AWS WAF works by defining custom security rules and policies to block malicious requests and mitigate web-based attacks.
- Further, you can integrate WAF with AWS Lambda for real-time alerts and automated threat response.
CASB (Cloud Access Security Broker):
Cloud Access Security Broker or CASB is the gatekeeper for the cloud environment and acts as a mediator between cloud service users and cloud service providers. This is to ensure that users use cloud applications securely and with compliance use.
Best utilization of the tool
- You can implement CASB solutions to gain visibility into the cloud services and applications utilized by your employees and accordingly assess the risk associated with the usage.
- You can utilize CASB to apply data protection policies and encryption mechanisms for cloud-based applications and services that are hostel on AWS.
- Furthermore, you can integrate CASB with AWS IAM for implementing security through role-based access controls (RBAC).
IAM (Identity and Access Management):
As the name suggests, IAM allows for the right access to the right user. It is part of the AWS security technology that is leveraged for managing digital identities and access to their IT resources.
Best utilization of the tool
- You can leverage IAM to manage the identities of users, their roles, and permissions within AWS environments. This allows for role segregation.
- You can utilize IAM policies to control access to any AWS resource and authenticate users securely.
- IAM enables you to enforce multi-factor authentication (MFA) for increased digital security.
- Leverage IAM roles for applications and services running on AWS EC2 instances, granting temporary credentials and fine-grained access controls.
SIEM (Security Information and Event Management):
SIEM will enable your organization to manage the IT infrastructure in its entirety. This includes collecting, correlating, analyzing and managing security-related information and data.
Best utilization of the tool
- You can utilize SIEM to analyze the generated logs and security events by AWS services.
- Through SIEM, you gain real-time insight into security threats and compliance violations across the AWS cloud environment.
- Integrate SIEM with AWS CloudTrail and AWS Config for comprehensive and complete security management.
In conclusion, the best utilization of AWS cloud security technologies such as CSPM, CWPP, WAF, CASB, IAM, and SIEM depends upon the specific security requirement. It is crucial for organizations to implement these technologies to ensure complete security of sensitive data, including employee data, client records, and financial information. By migrating data management to the AWS cloud, you can enhance the security, scalability and stability of data within your organization in compliance with global data protection protocols.