Project Overview
Demonstration of DevOps project implementation on AWS Elastic Kubernetes Service (EKS) with nearly full automation. That includes automation of infrastructure provisioning, code quality check and build, deployments via gitops methodology, monitoring, logging and alerting.
Table of Contents
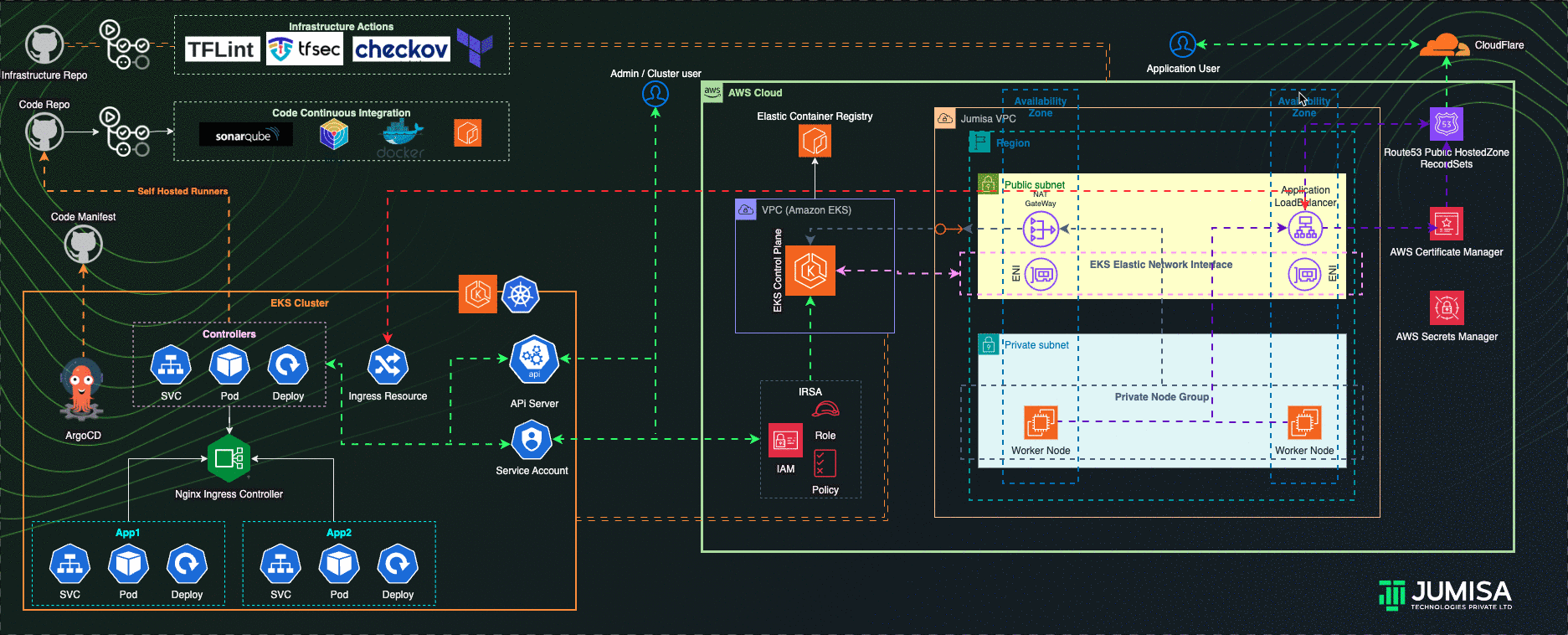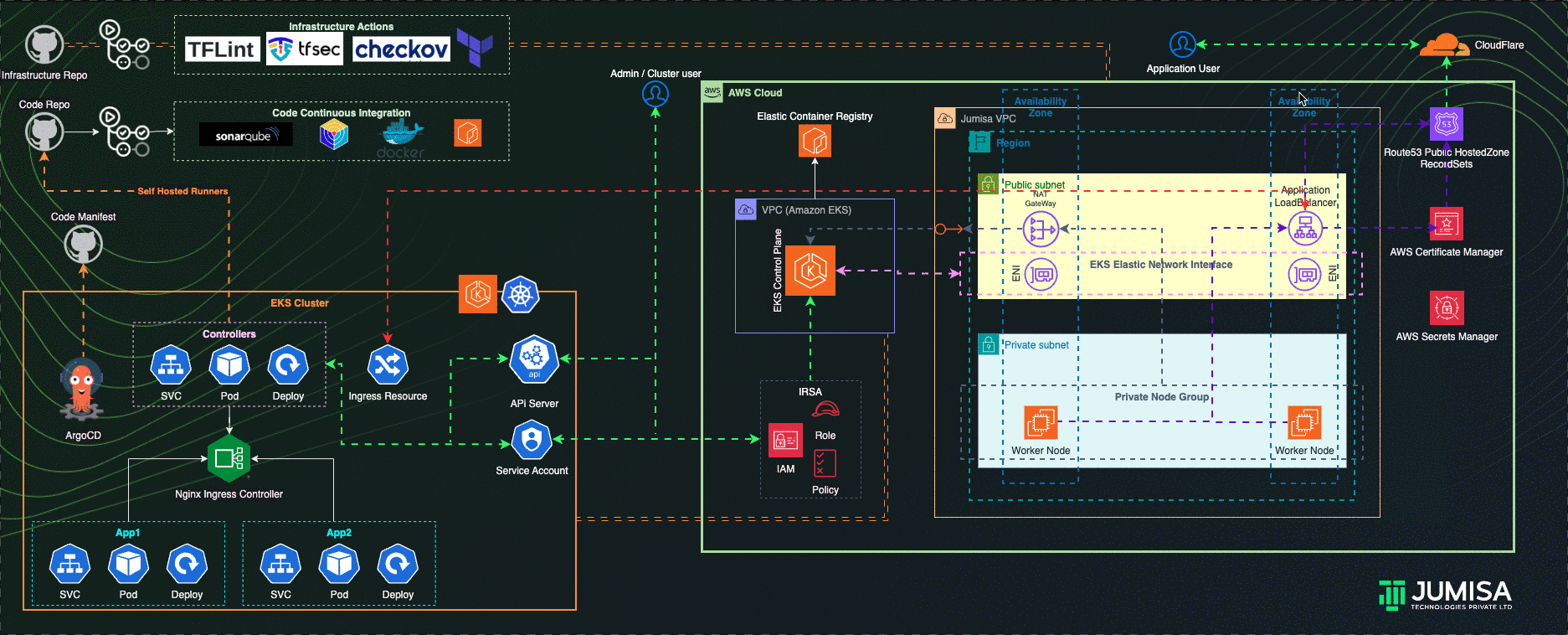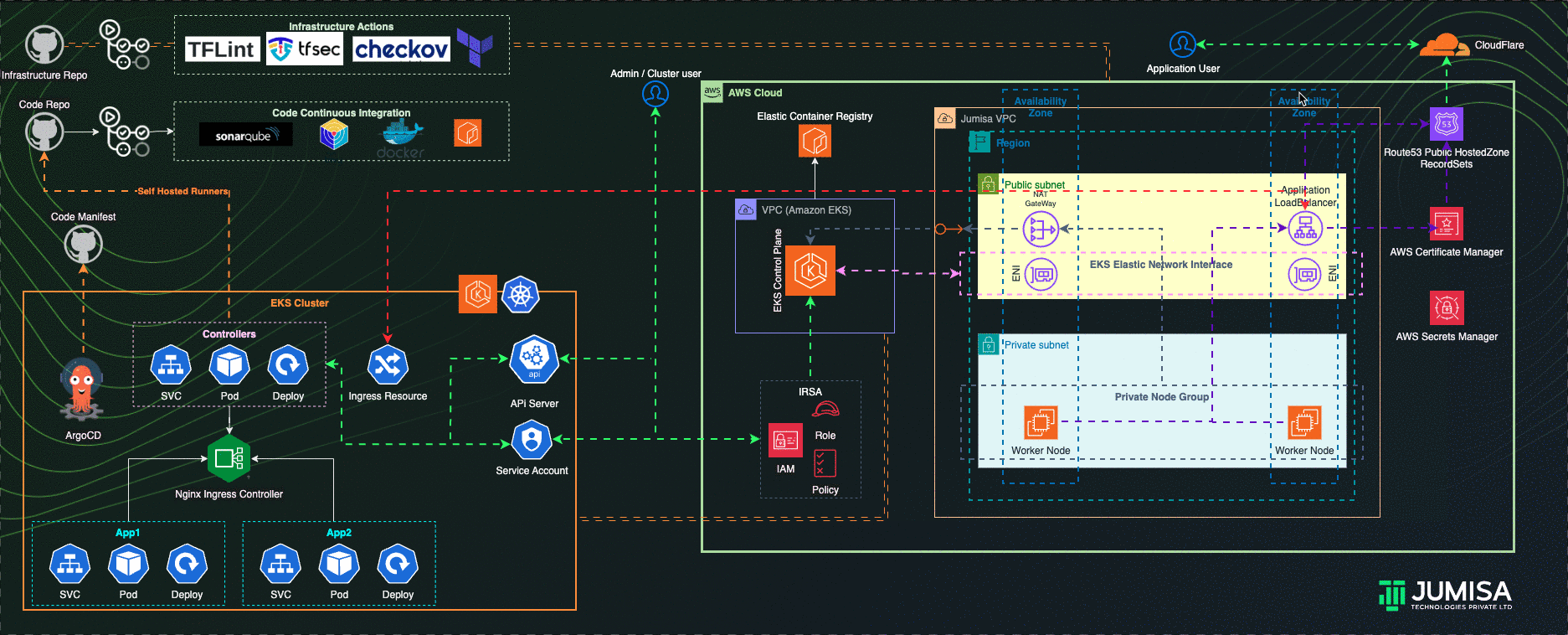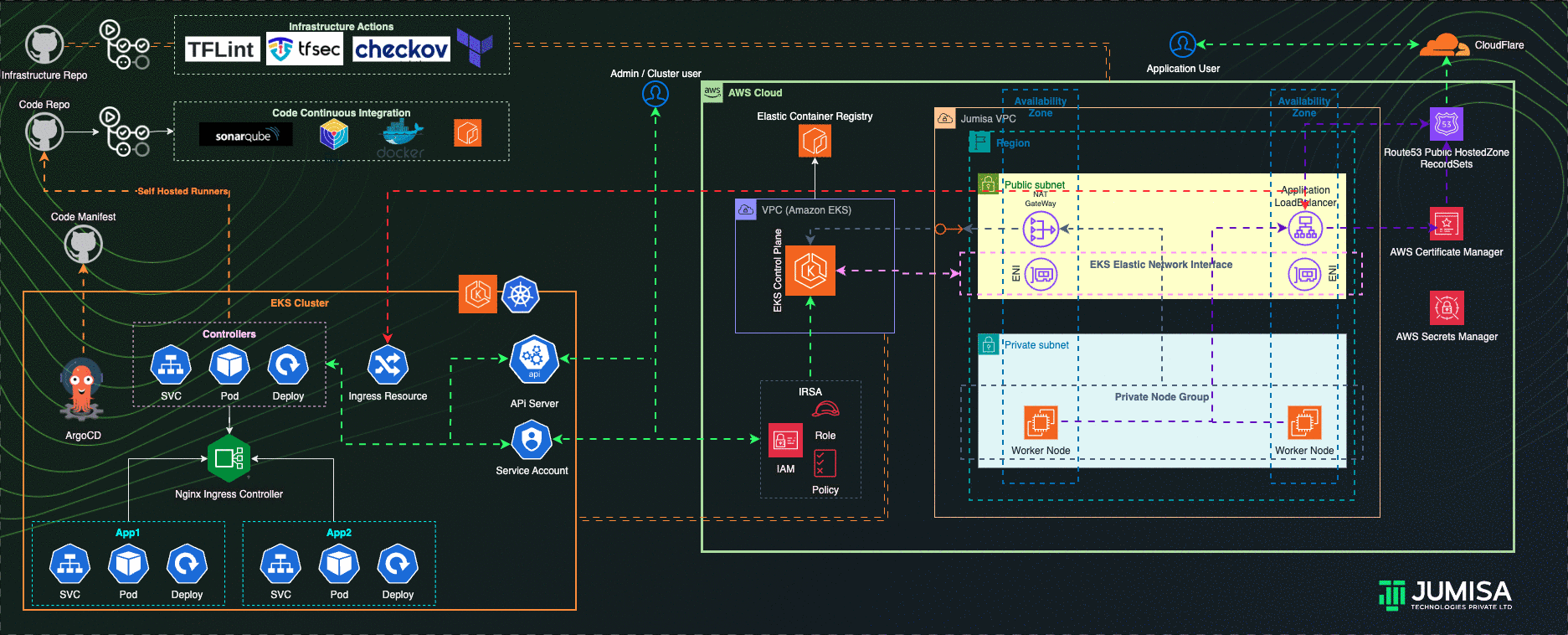
Architecture Overview
- GitHub Actions Workflows used for the iteration of Infrastructure and Application code builds
- Terraform is used for building the complete infrastructure
- Our Domain is registered with Cloudflare
- AWS Route53 Public Hosted zone is created and NS mapped to Cloudflare domain
- AWS Certificate Manager (ACM) is used to create SSL certificate for the domain name and signed by DNS method (record added Route53 hosted zone)
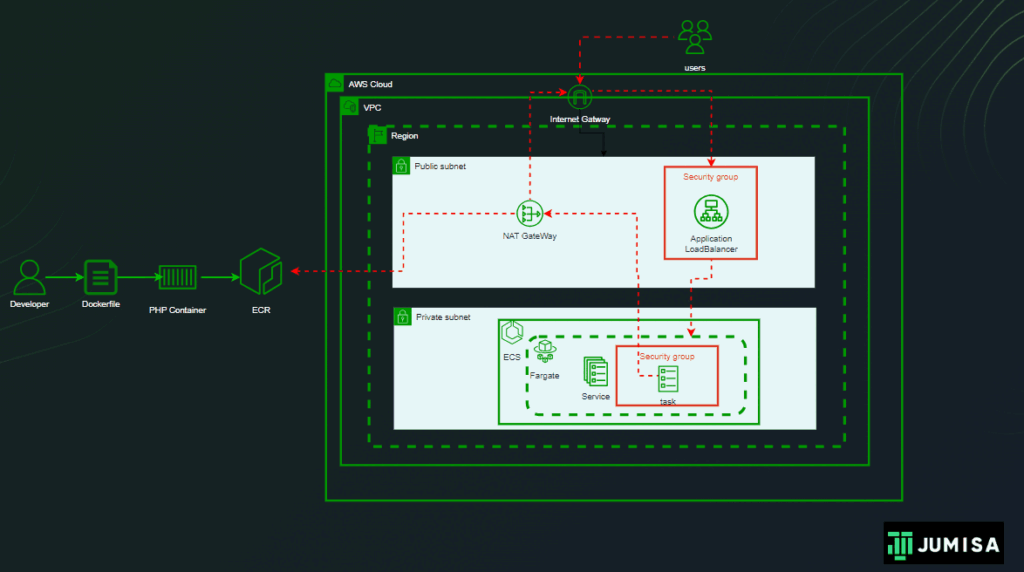
- EKS Cluster and worker node groups in private subnet provisioned with Kubernetes version 1.27.
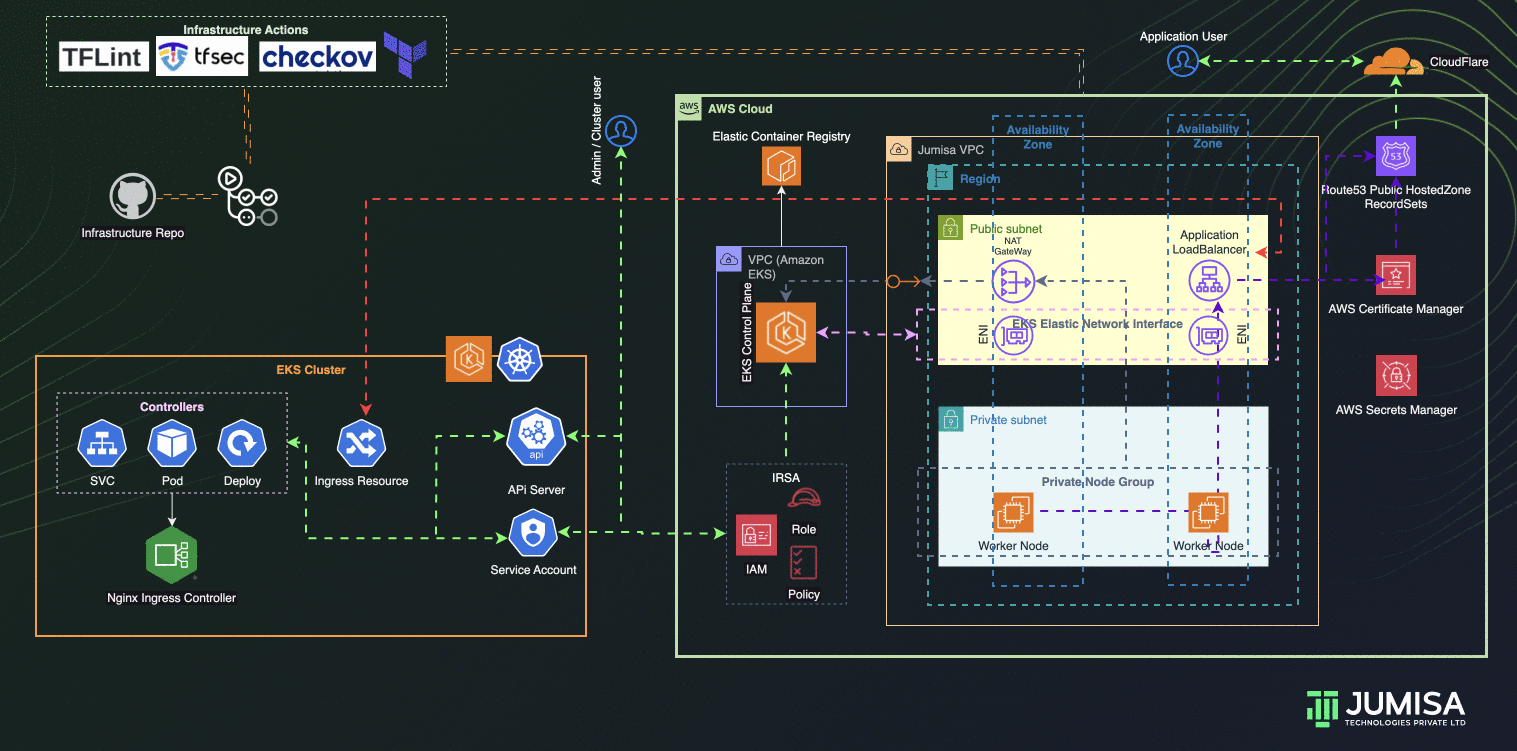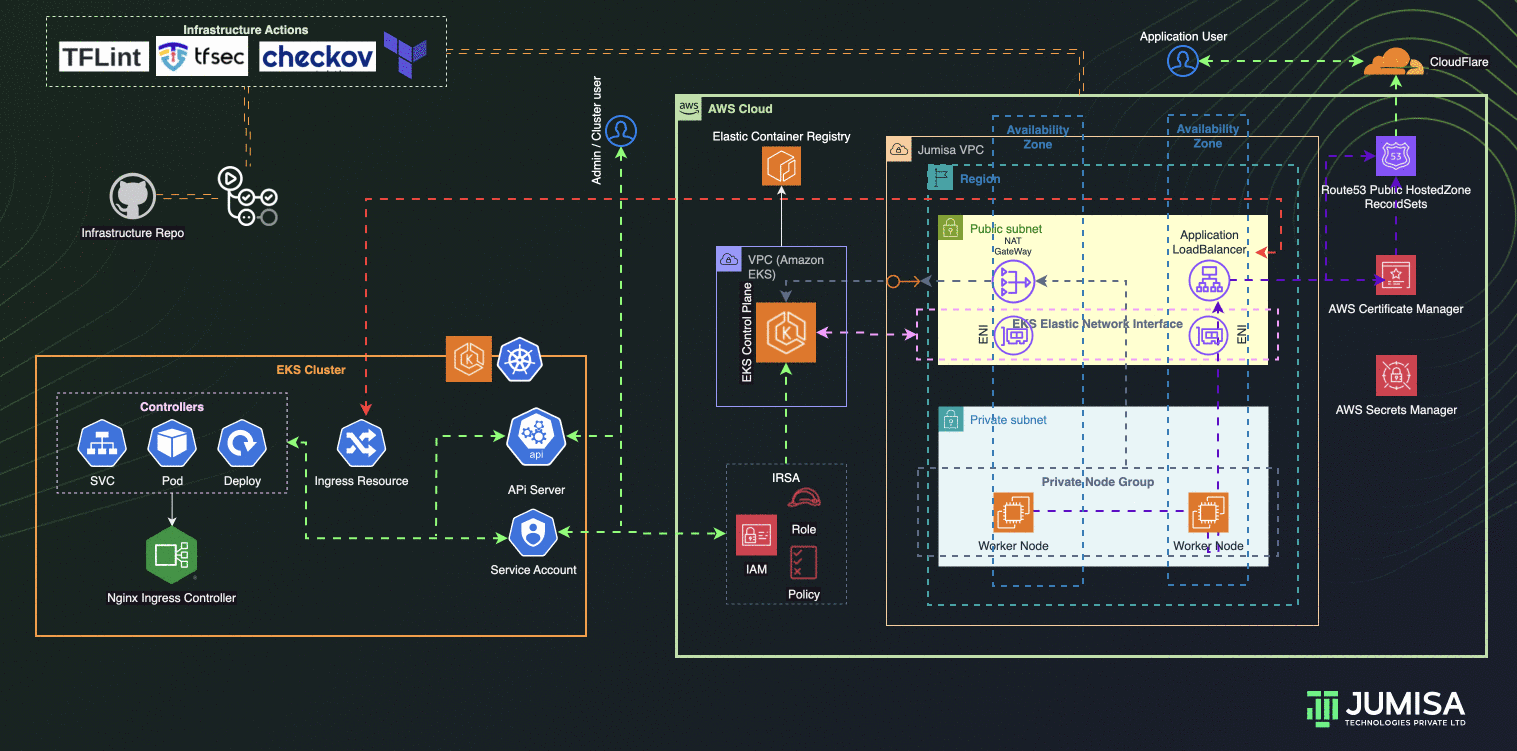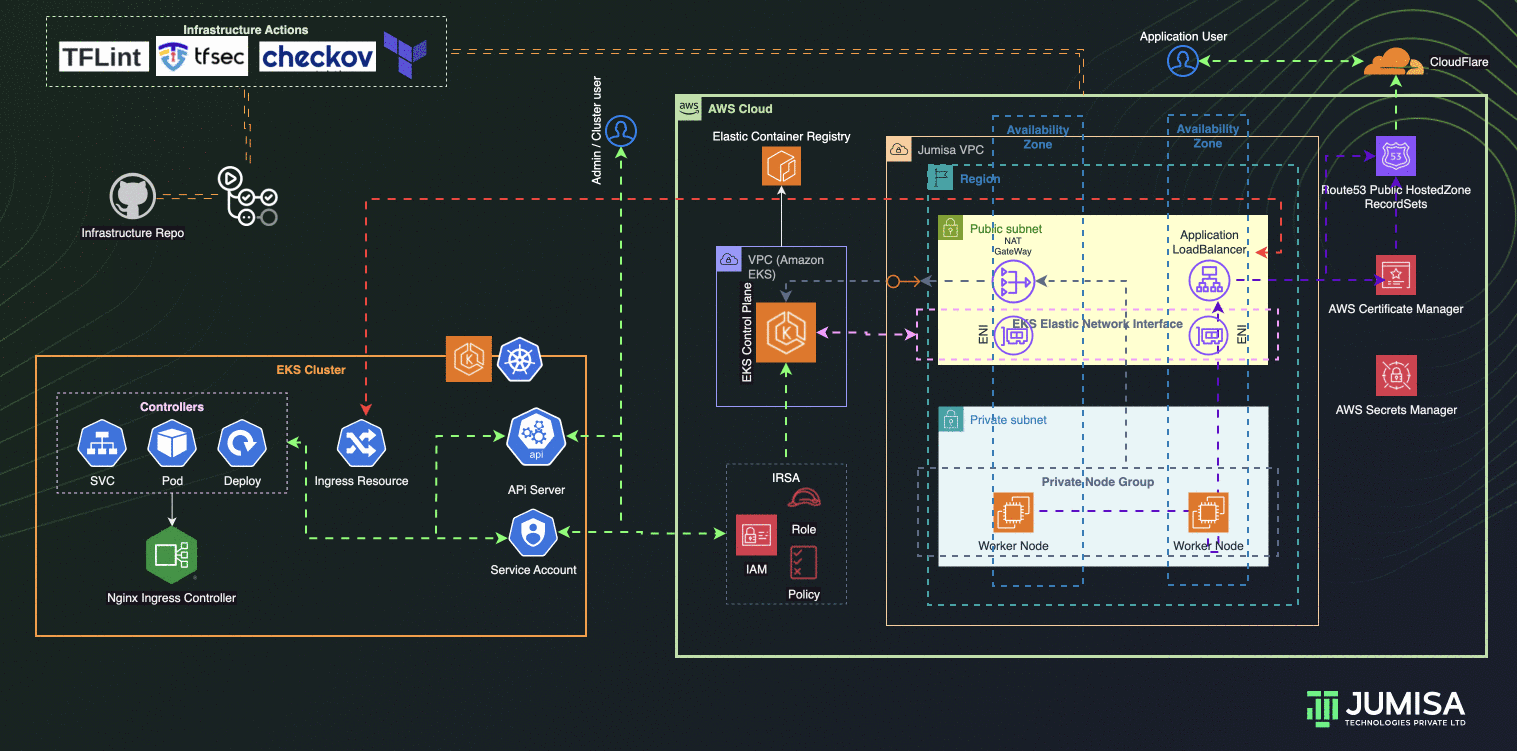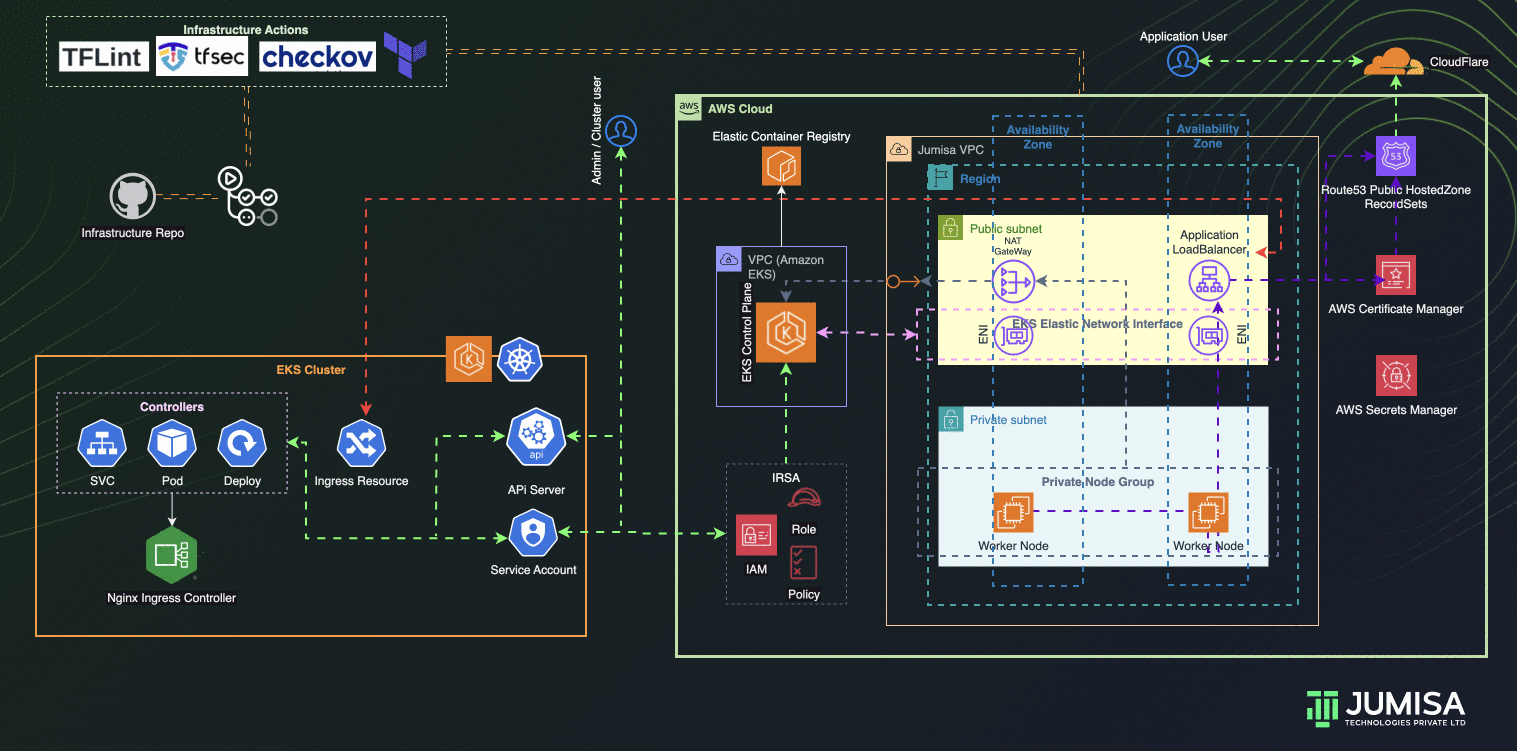
- AWS Load Balancer Controller configured to provision AWS Application Load Balancer (ALB) with wildcard mapping as targeted to EKS Private Node groups
- Nginx Ingress Controller configured to handle any routes such as host , path based from the eks cluster resource
- External DNS Controller configured to add the AWS ALB DNS to Route53 recordset. Filtered only to scan AWS LB Controller ingress resources.
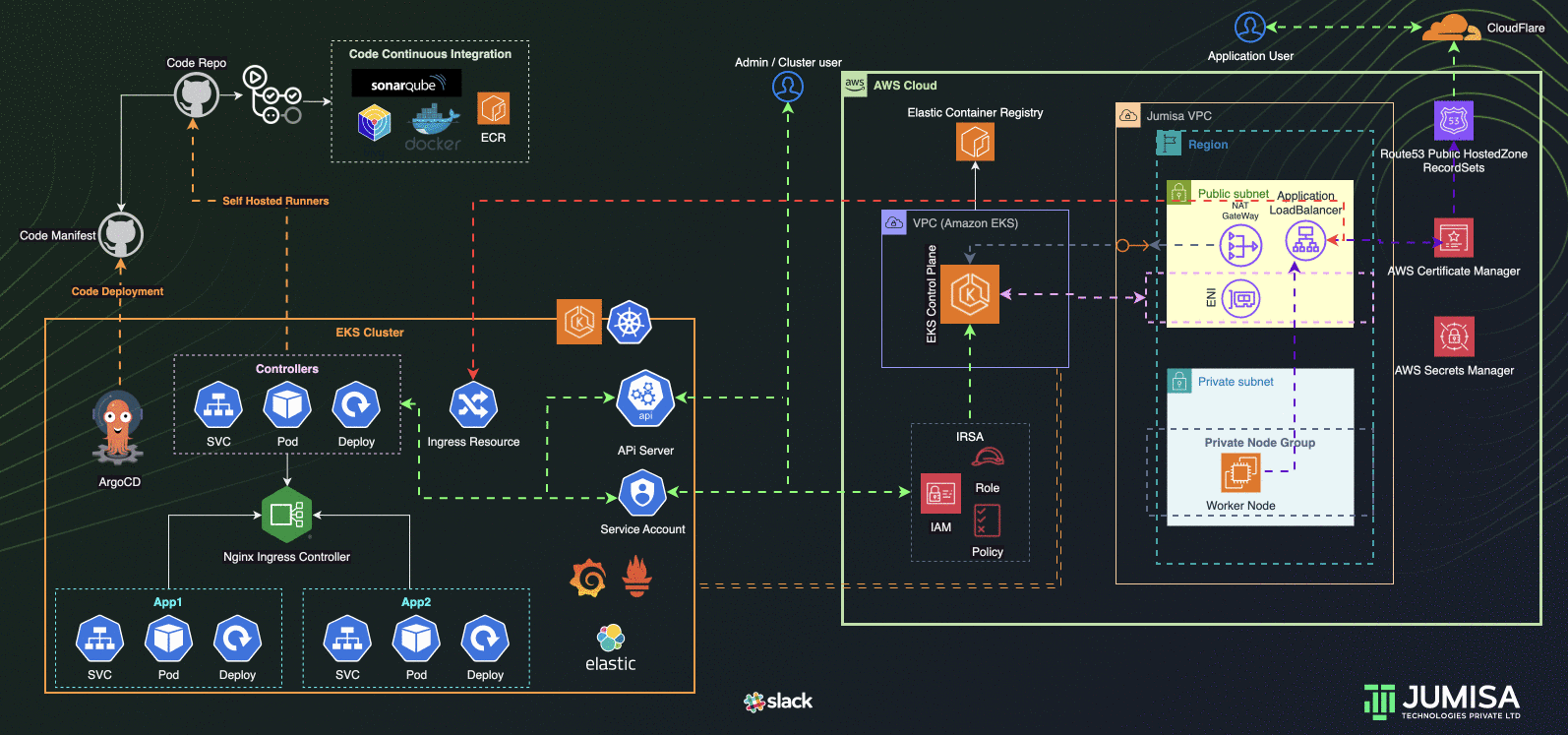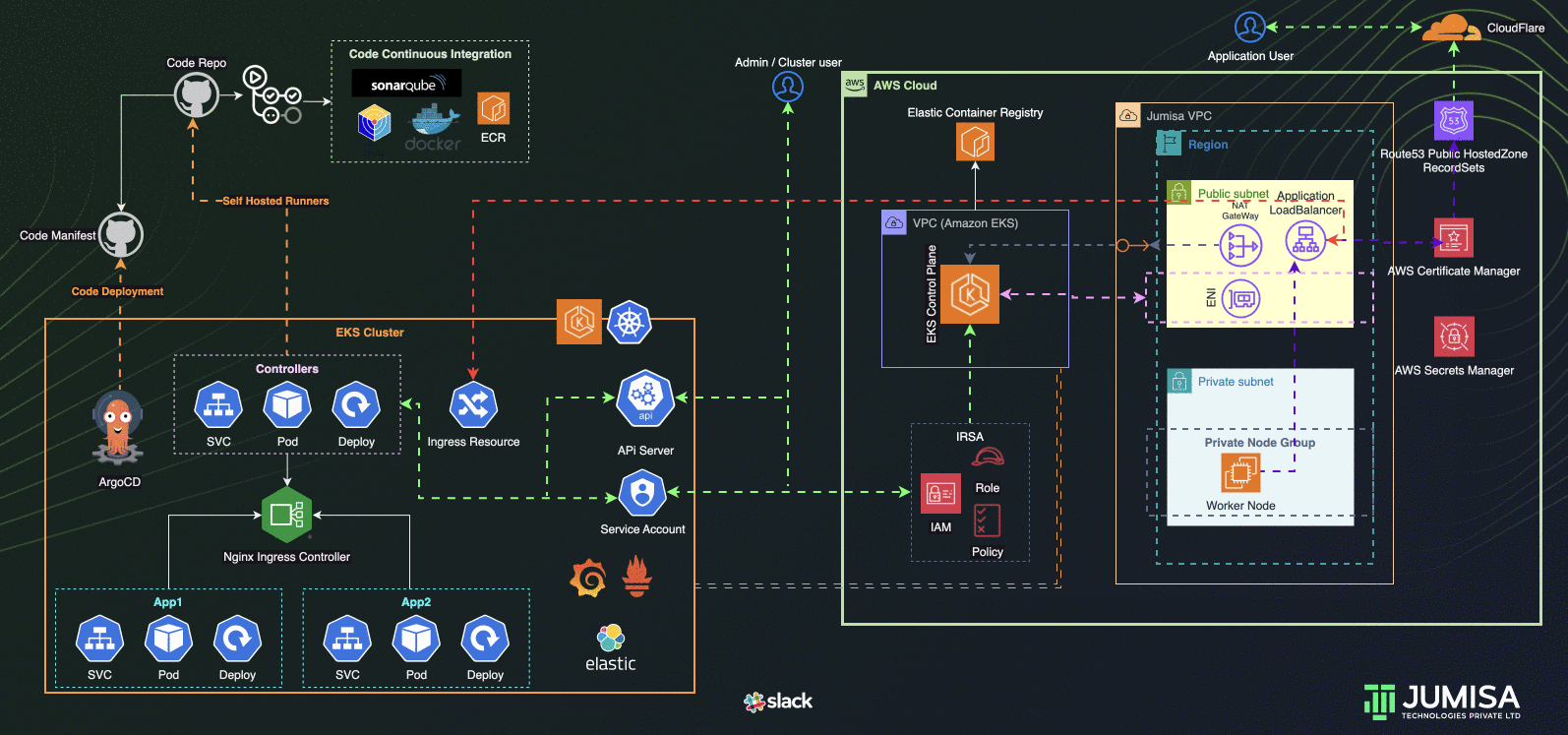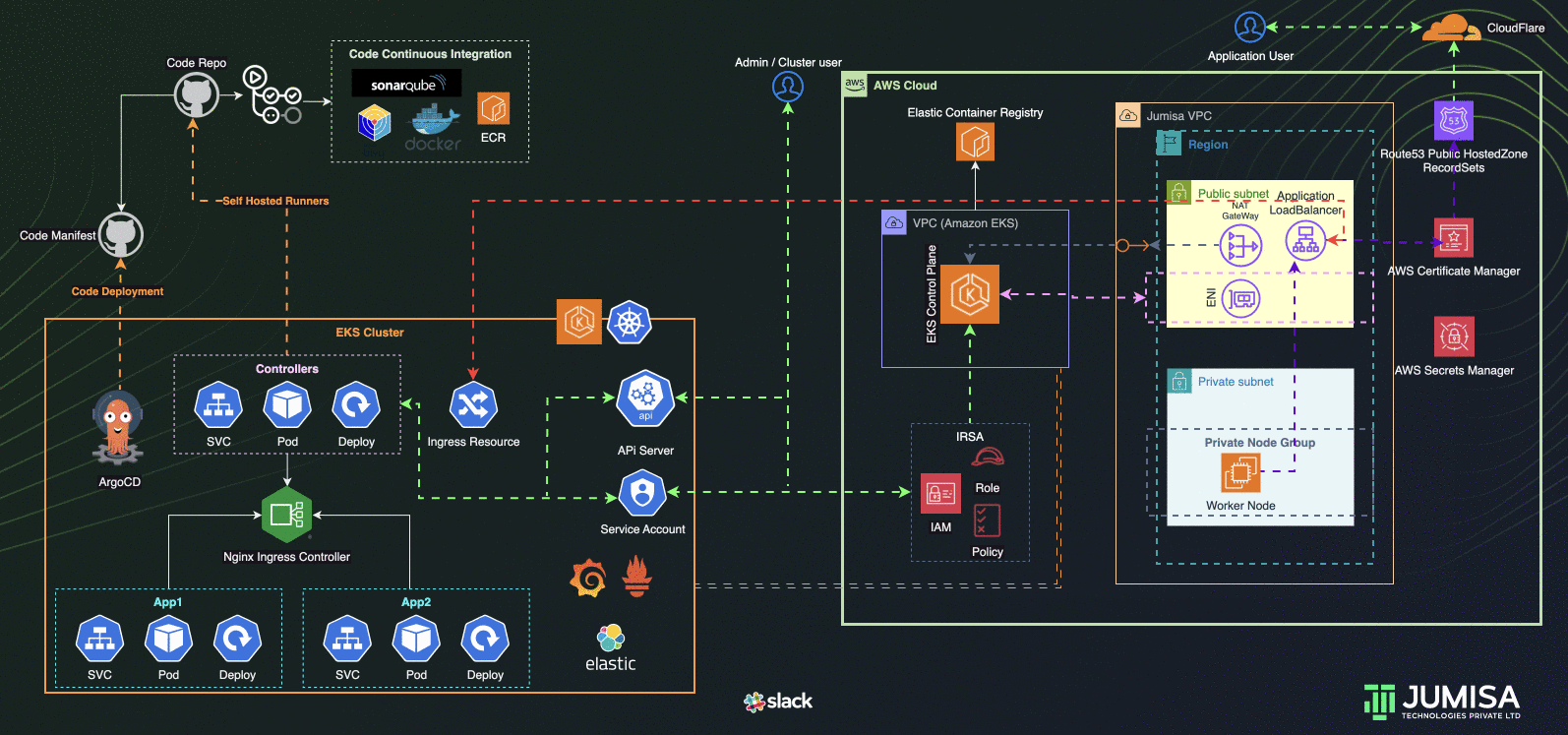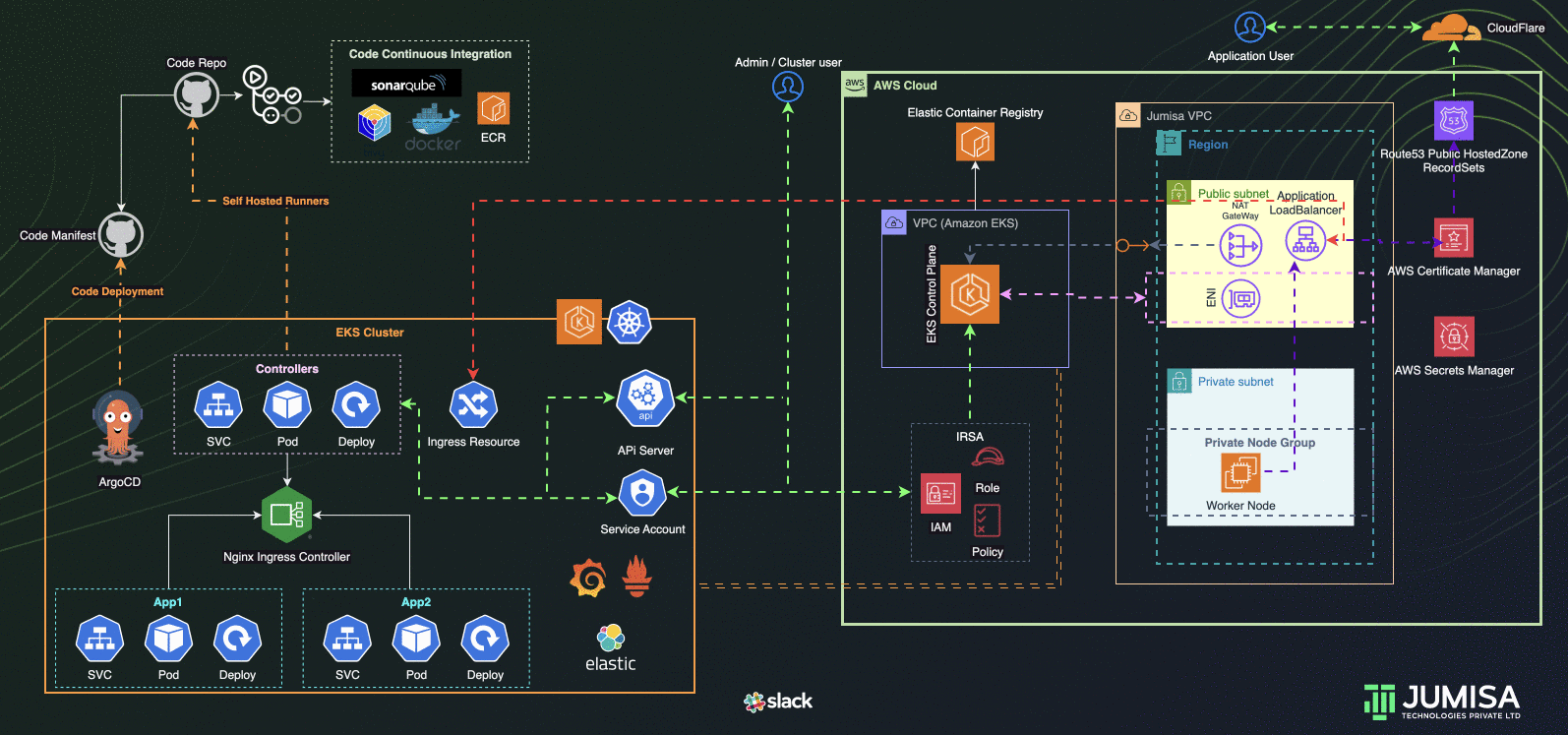
- GitHub Actions Controller configured to add Self-Hosted Runners to code/application and tools github repositories
- ArgoCD configured to handle the application and tools deployment
- IAM Role Based Service Account (IRSA) are configured to allow the Kubernetes resources access, manage AWS Resources
- Role Based Access Controls (RBAC) are used to manage the access to the users to connect to Kubernetes API via cli or any ide
- Infrastructure code scans are carried out by TFlint, TFSec, Checkov through GitHub Actions using managed runners
- Application code scan and builds by Sonarqube, Trivy and Docker through GitHub Actions using Self-hosted runners
- Prometheus, Grafana, Elastic Fluentd Kibana Stacks as the part of traceability solution are configured in the cluster
- Slack integration for notification from GitHub Actions, traceability tools
- Community and Custom Helm Charts are used for deploying controllers, application and tools manifests to the cluster
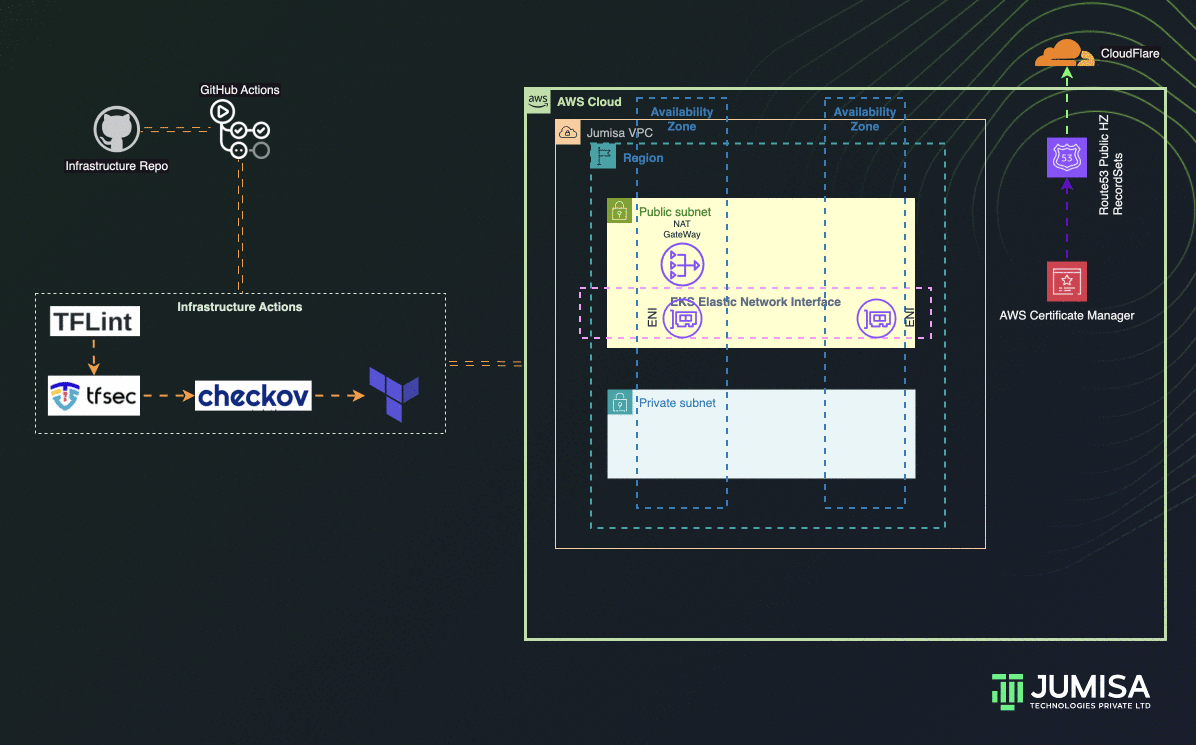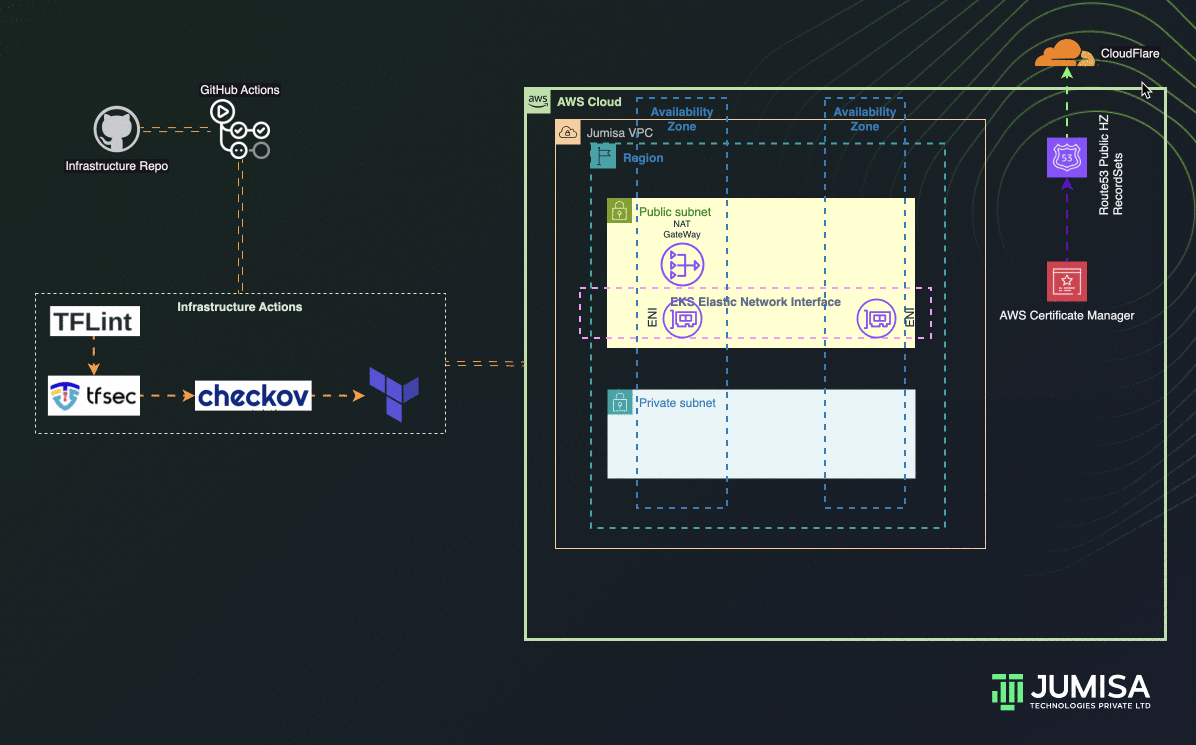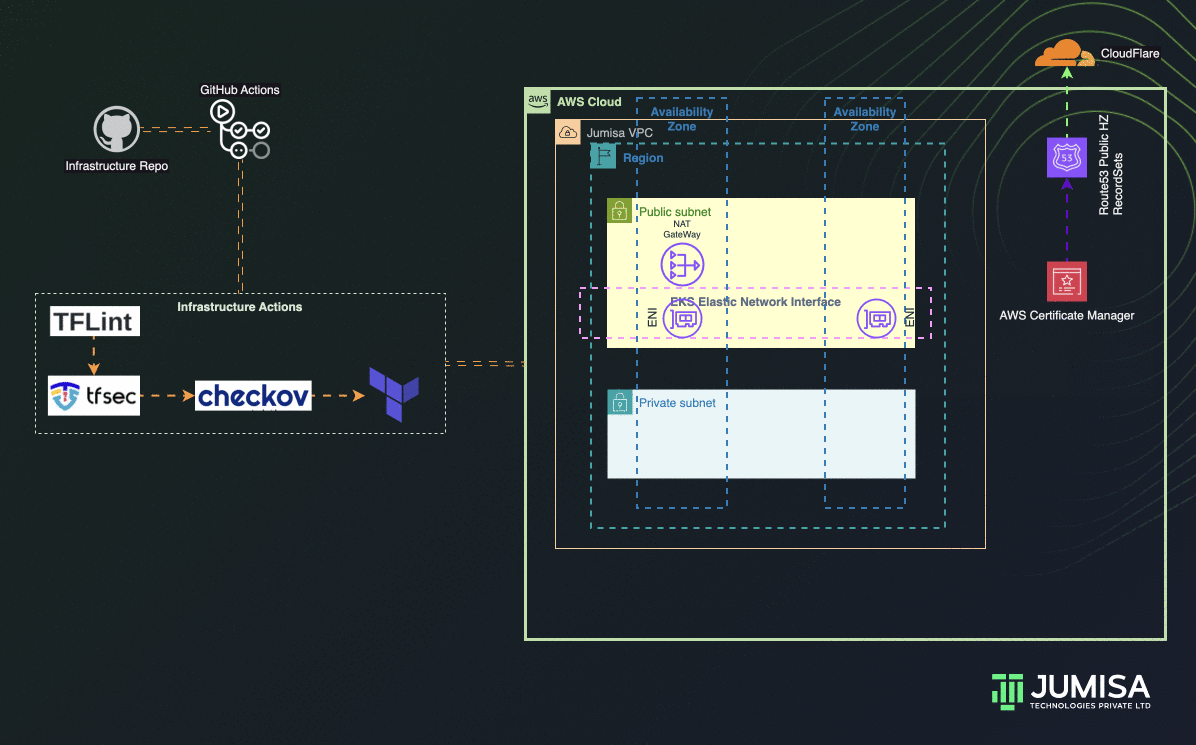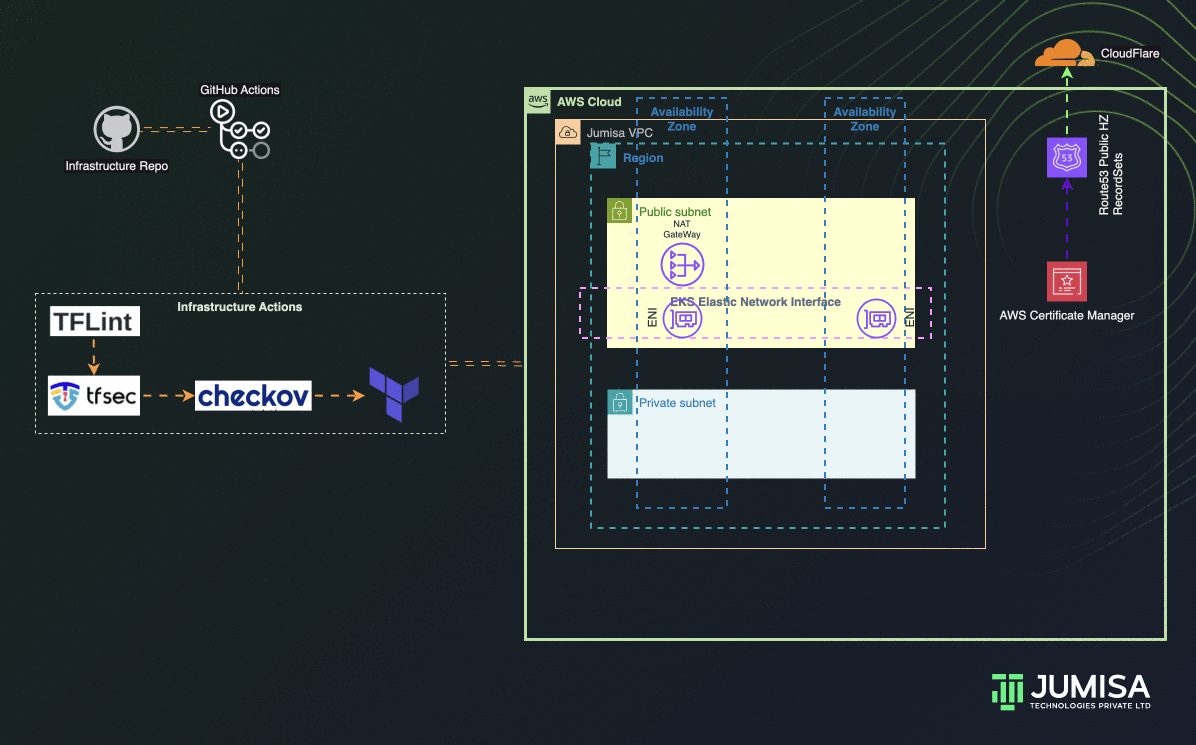
Phase 1: Network Resources
- Building GitHub Workflows to scan Terraform Code with TFLint, TFSec and Checkov
- Terraform AWS Provider and AWS network resources such as VPC, Routes, Route Tables, Subnets, Route53, Cloudflare, SSL, etc
- Terraform deployment post review and manual approval from GitHub
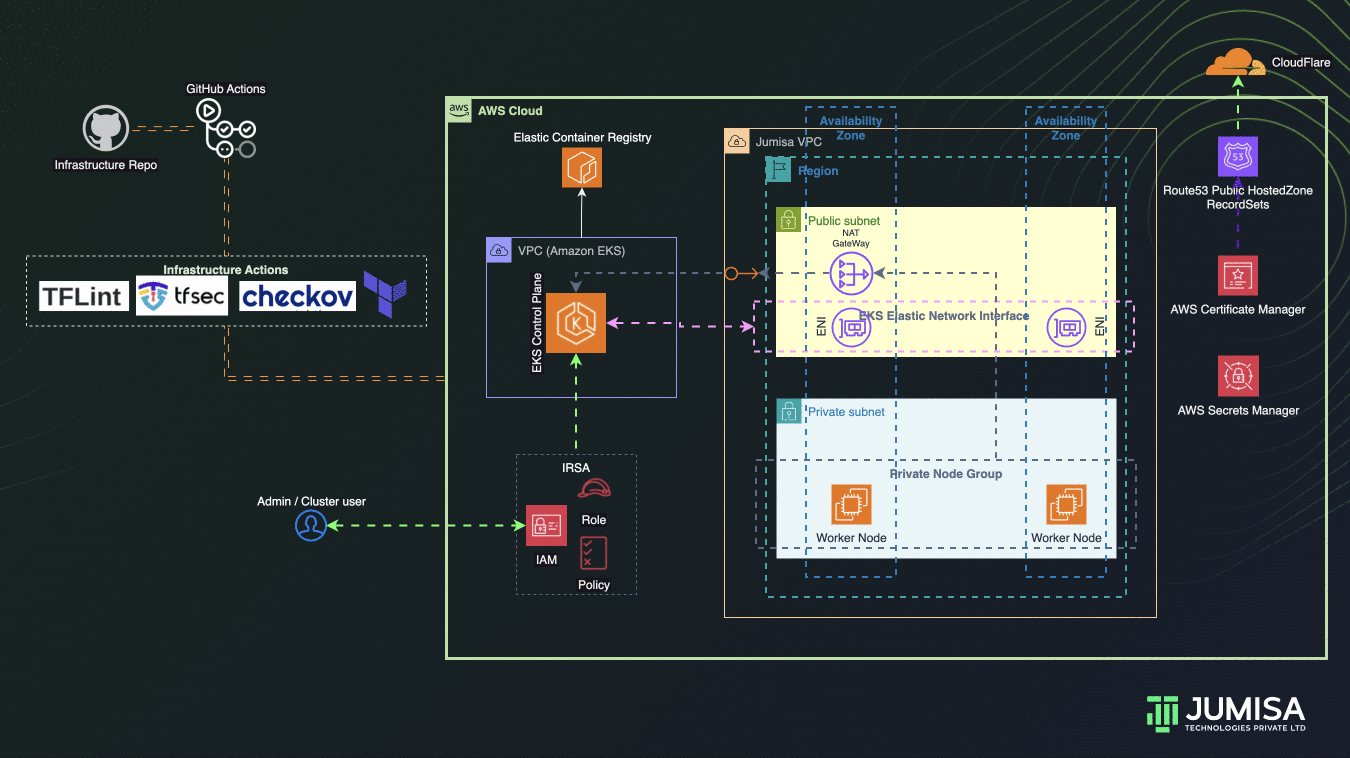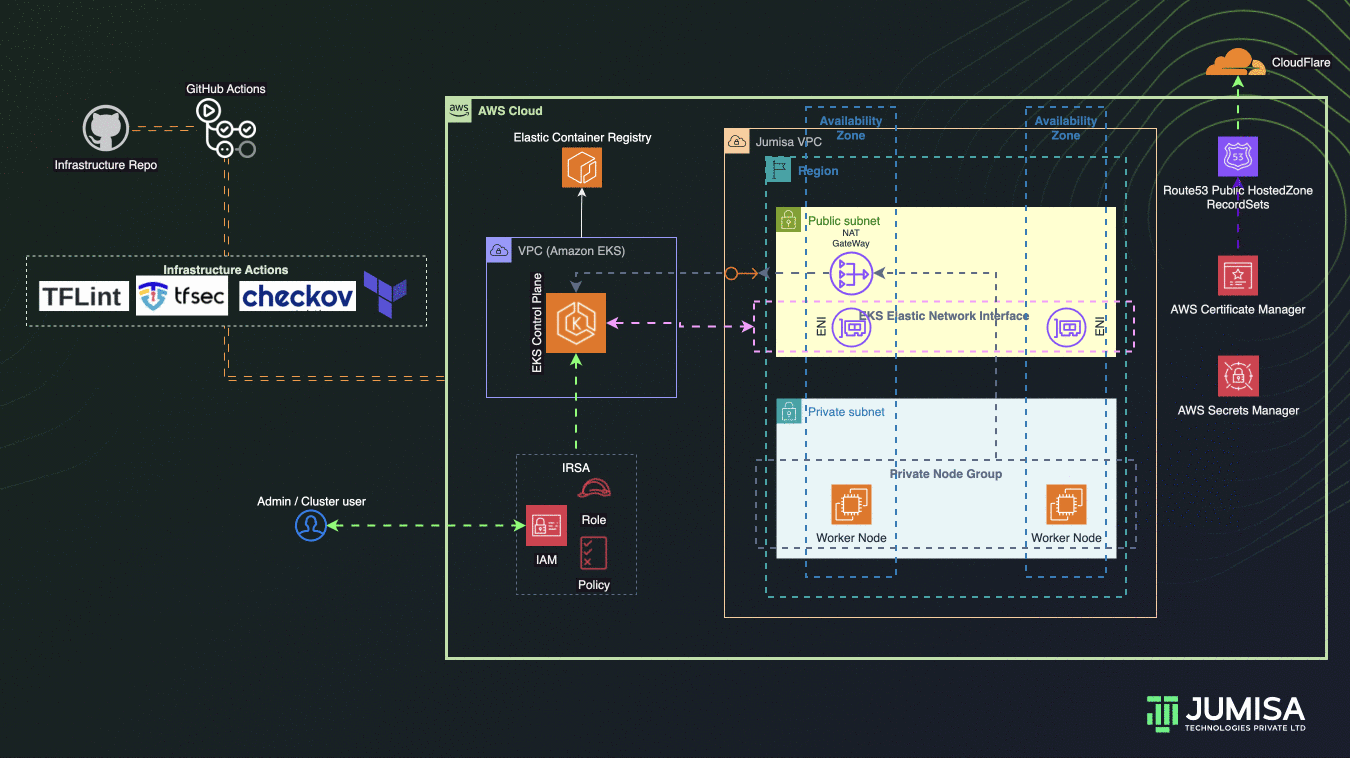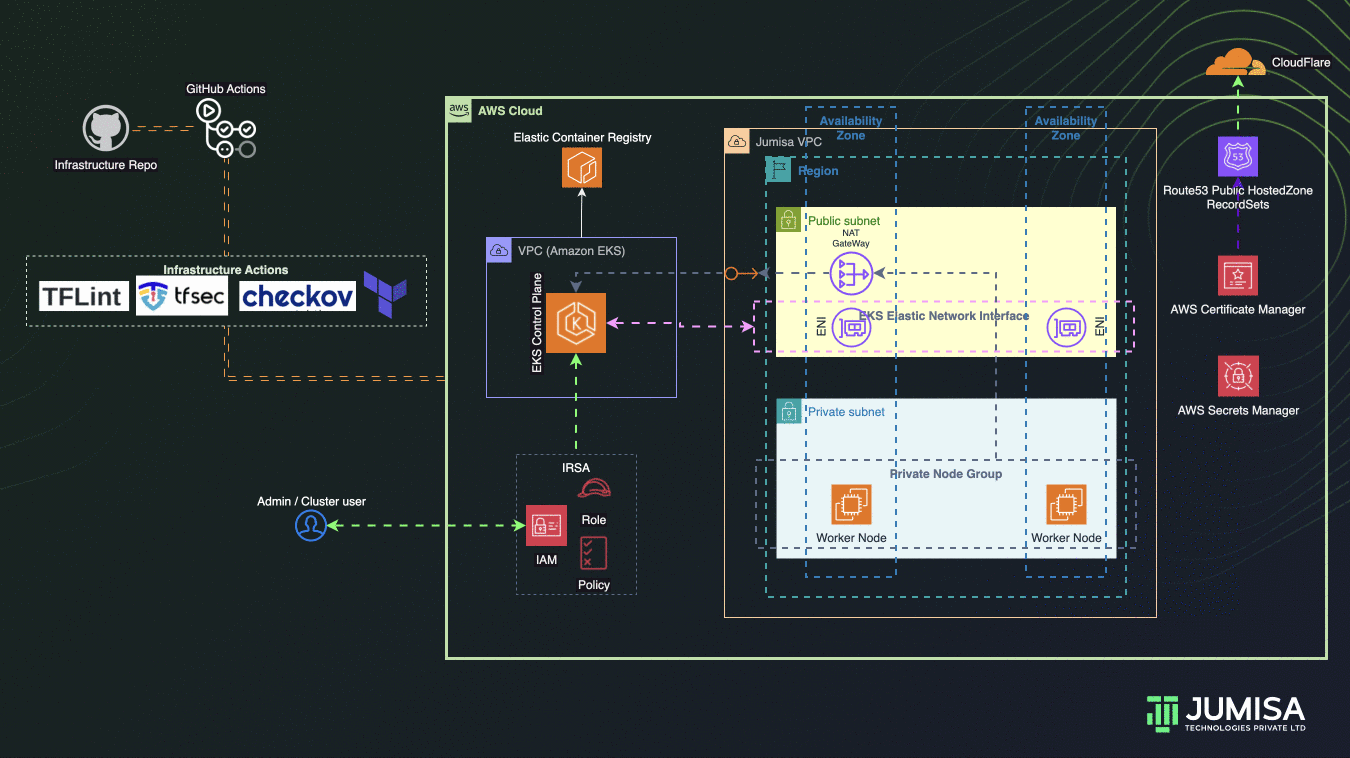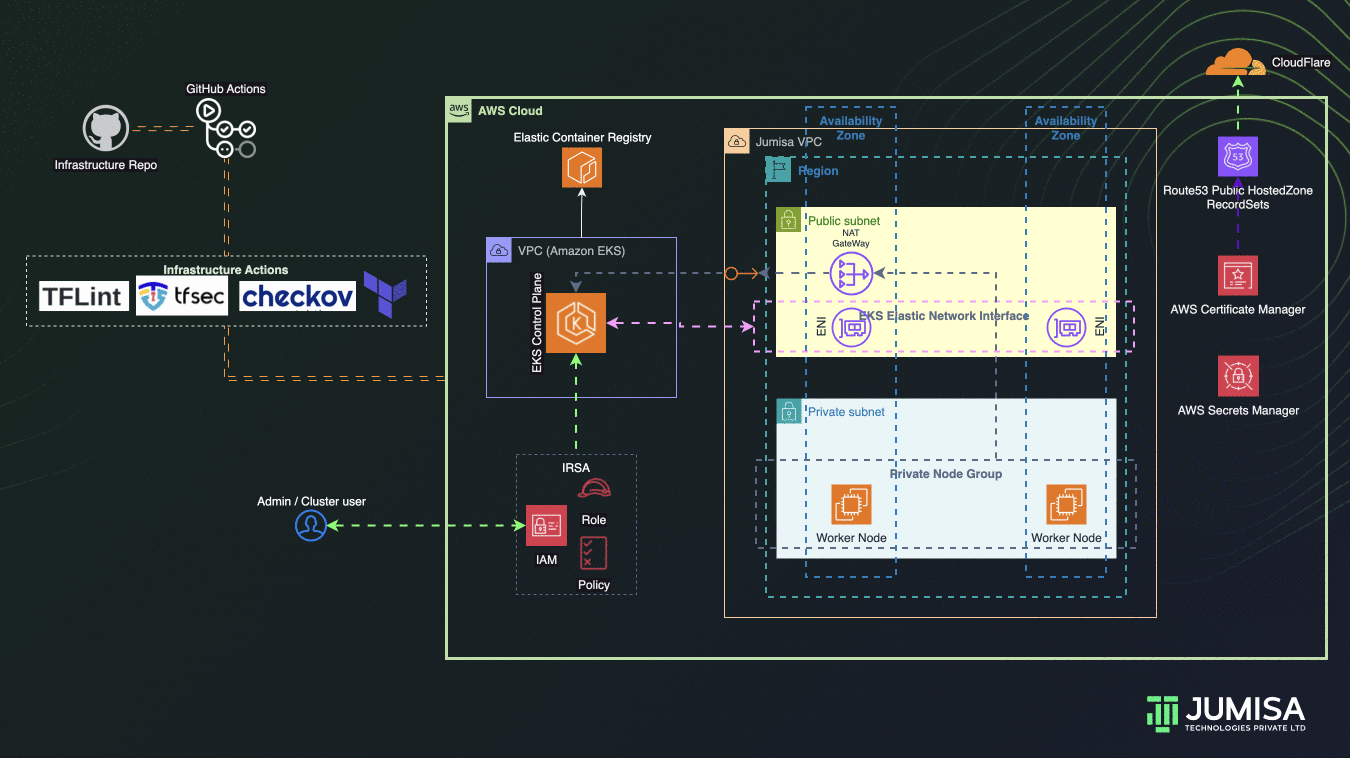
Phase 2: Cluster Setup
- Create EKS Cluster, Node Groups
- Create OIDC provider, IAM roles
- Kubectl config to validate the nodes and Kubernetes default resources
Phase 3: Authentication & Authorization
- Create IAM Roles, Groups for the user, developers
- Create cluster role, cluster role binding, role, role binding for specific namespaces
- Update aws-auth for the roles
- Kubectl api call to validate the access policies defined
Phase 4: Ingress, DNS Controllers
- Create AWS Load Balancer Ingress Controller
- Create Nginx Ingress Controller
- Create External DNS Controller
- Create Ingress resource to provision AWS Application LoadBalancer with record sets on Route53 Hosted Zone
Phase 5: GitHub EKS Self-Hosted Runners
- Create GitHub Actions Runners Scale Set Controller
- Create GitHub Runners and associate with code/tool github repositories
- Review the Runner and Runner Group in GitHub Actions
Phase 6: CI CD Process for Application Code
- GitHub Self Hosted Runners are used for the Application build from GitHub Actions Workflows
- Sonarqube, Trivy Scan are implemented in Application code build phase
- Post successful, scan the application code is built and push to AWS Elastic Container Registry (ECR)
- Update the Code manifest repo with new build details
- GitOps Workflows with ArgoCD, verify Application code continuous deployment
Phase 7: Traceability Solution
- Create Prometheus , Grafana for monitoring and alerting
- Create Elastic FluentD Kibana Stack for logging
- Integrate Slack for notification
Next Steps
Thanks for your attention and patience to read this article.
Next step is to setup GitHub Actions, Terraform and AWS Network resources, follow them on
Phase 1 : Network Resources
Demo Series: EKS TF GHA GitOps : Phase 1 – Network Setup
Happing reading !!! Let us learn together !!!