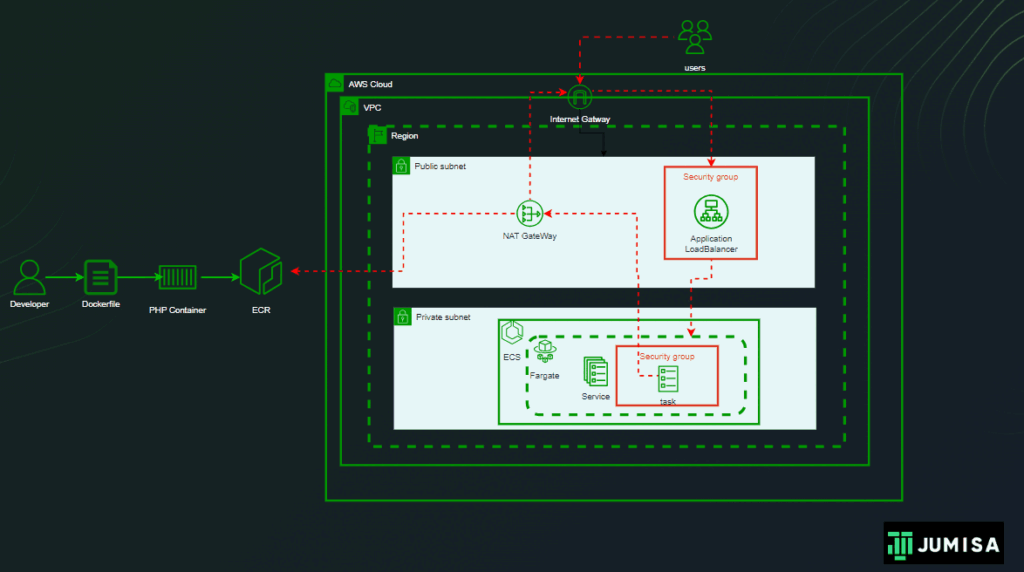
In the era of digital transformation, businesses are increasingly migrating their operations to the cloud. This shift brings numerous benefits, such as scalability, flexibility, and cost-efficiency. However, it also introduces new security challenges. For DevOps teams, ensuring robust cybersecurity in the cloud is paramount. This guide provides practical insights into how DevOps teams can fortify their cloud environments against cyber threats.
Understanding the Shared Responsibility Model
One of the first steps in cloud security is understanding the shared responsibility model. In cloud computing, security responsibilities are divided between the cloud service provider (CSP) and the customer. The CSP is responsible for the security of the cloud infrastructure, while the customer is responsible for securing their data, applications, and configurations within the cloud.
For instance, in an Infrastructure as a Service (IaaS) model, the CSP handles the physical data center, networking, storage, and servers, while the customer must secure their operating systems, applications, and data. Knowing where the provider’s responsibility ends and yours begins is crucial for effective security management.
Implementing Strong Identity and Access Management (IAM)
Identity and Access Management (IAM) is a cornerstone of cloud security. It involves defining and managing the roles and access privileges of individual users and devices. Effective IAM ensures that only authorized users can access specific resources, minimizing the risk of unauthorized access.
Best Practices for IAM:
- Least Privilege Principle: Grant users the minimum level of access necessary to perform their duties. This reduces the potential impact of compromised credentials.
- Multi-Factor Authentication (MFA): Implement MFA to add an extra layer of security. Even if credentials are stolen, MFA makes it harder for attackers to gain access.
- Regular Audits: Regularly audits user accounts and permissions to ensure they align with current roles and responsibilities.
Securing Cloud Data
Data security is another critical aspect of cloud security. Protecting data both at rest and in transit is essential to prevent breaches and ensure compliance with regulations.
Strategies for Data Security:
- Encryption: Always encrypt sensitive data, both at rest and in transit. Use strong encryption standards and ensure encryption keys are securely managed.
- Data Masking: Use data masking techniques to obfuscate sensitive information in non-production environments, reducing the risk of exposure.
- Backups: Regularly back up data and ensure backups are securely stored and encrypted. This helps in recovery from ransomware attacks and data loss incidents.
Implementing Continuous Security Monitoring
Continuous monitoring is vital for detecting and responding to security incidents in real-time. By integrating security monitoring into the DevOps pipeline, teams can identify vulnerabilities and respond to threats promptly.
Tools and Techniques for Continuous Monitoring:
- Security Information and Event Management (SIEM): SIEM systems collect and analyze security data from various sources, providing real-time alerts and insights into potential security issues.
- Intrusion Detection Systems (IDS): IDS tools monitor network traffic for suspicious activity and potential threats.
- Automated Security Scanning: Integrate automated security scanning tools into the CI/CD pipeline to identify vulnerabilities early in the development process.
Adopting DevSecOps Practices
DevSecOps is an approach that integrates security practices into the DevOps workflow. It emphasizes the importance of making security a shared responsibility across all stages of the software development lifecycle.
Key Components of DevSecOps:
- Shift-Left Security: Incorporate security early in the development process, starting from the design phase. This helps identify and mitigate security issues before they become costly to fix.
- Security as Code: Treat security configurations and policies as code, allowing them to be version-controlled, reviewed, and tested just like application code.
- Collaboration and Training: Foster a culture of collaboration between development, operations, and security teams. Provide ongoing security training to keep team members informed about the latest threats and best practices.
Securing the CI/CD Pipeline
The Continuous Integration and Continuous Deployment (CI/CD) pipeline is a critical component of the DevOps workflow. Securing this pipeline is essential to prevent attackers from injecting malicious code into the production environment.
Best Practices for CI/CD Security:
- Code Signing: Use code signing to verify the integrity and authenticity of code before it is deployed.
- Secrets Management: Securely manage secrets such as API keys, passwords, and certificates. Use dedicated secrets management tools to avoid hardcoding sensitive information.
- Environment Segmentation: Segment development, testing, and production environments to minimize the risk of cross-environment contamination.
Conclusion
Ensuring security in the cloud is a multifaceted challenge that requires a proactive and comprehensive approach. By understanding the shared responsibility model, implementing strong IAM, securing data, adopting continuous monitoring, embracing DevSecOps practices, and securing the CI/CD pipeline, DevOps teams can build resilient and secure cloud environments.
The dynamic nature of cybersecurity threats demands continuous vigilance and adaptation. By fostering a culture of security and integrating best practices into everyday operations, DevOps teams can effectively safeguard their cloud infrastructure and maintain the trust of their users and stakeholders.